With attacks on the rise and people becoming tired of authenticator alerts (which leads to them just accepting anything), now is the time to start looking at alternatives, uncluding Fido2
I was lucky enough to be sent a Fido 2 K33 device from Feitian technologies to give a thorough testing. Whilst I’ve been sent the device for testing, I have NOT been paid for this review, these opinions are my own and completely unbiased.
- Unboxing
- Features
- BioPass Windows Application
- Setting up Bluetooth
- Windows Hello Login
- M365 MFA
- Azure MFA
- Twitter MFA
- Gmail MFA
- Outlook.com MFA
The hardware
Starting with the hardware, it comes in a simple cardboard box and is literally just the device, no cables or instructions included, but I’m sure everyone has a USB-C cable these days


The device itself is small and light enough to fit on a set of keys, on-off button on the right hand side and a large fingerprint on the front.

Prior to unboxing, make sure you give it a good charge before using
Hardware Support & Features
The K33 has some advantages over the other Feitian options. Firstly the fingerprint gives an extra layer of protection to avoid someone grabbing the device and simply using it to authenticate (especially useful if on a set of keys).
It also features USB, Bluetooth and NFC connectivity so is completely cross-platform (there’s even a Linux application), although I personally found Bluetooth to work more reliably than NFC.
One thing to note, if you switch to MFA for everything and have this as the ONLY secondary authentication, if you lose it, you are stuck. A few sites will give you a backup/emergency code (listed below), but I’d always suggest having a secondary authentication option, even something like SMS, or a second FIDO2 key.
Application for Windows
The K33 will work out of the box with Windows 10 or Windows 11, but if you want more control over the device itself, the BioPass manager app (available in the Windows store), works well and lets you rename fingerprints which is always a bonus.
First Setup
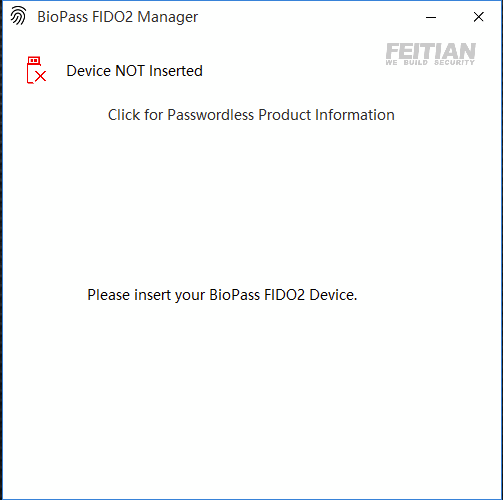
To configure with the app, you’ll need to plugin to the USB-C on the bottom of the unit.
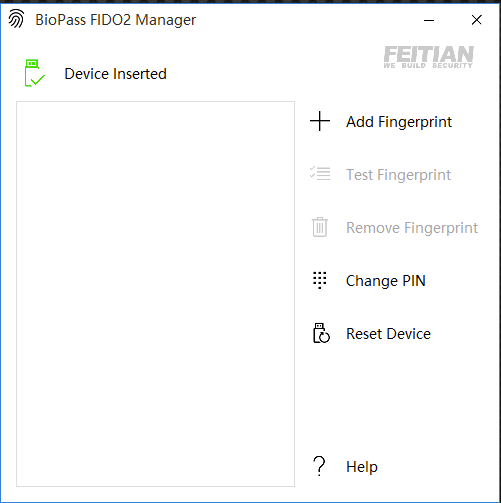
Once plugged in, you can setup a PIN or add fingerprints onto the device:
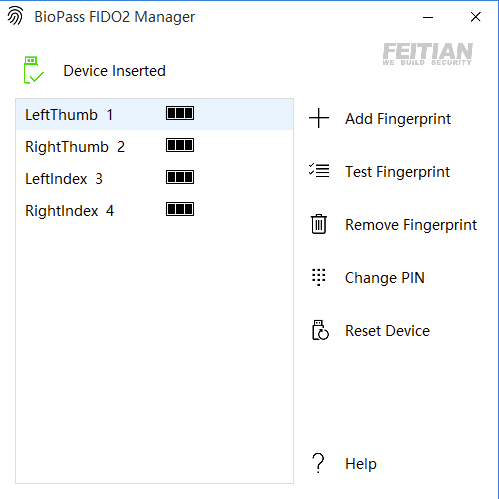
Once added, double clicking on a fingerprint gives the option to rename, I’ve added the ones I’m most likely to use when I pick it up:
Bluetooth
To enter pairing mode, press and hold the button on the side for 5 seconds
On my machine, it displayed as the following, but yours may be different
Windows Login
The first thing I want to do is add this as a Windows Hello authentication method (via bluetooth, I don’t like too many wires)
Navigate to Settings – Accounts – Sign-in Options
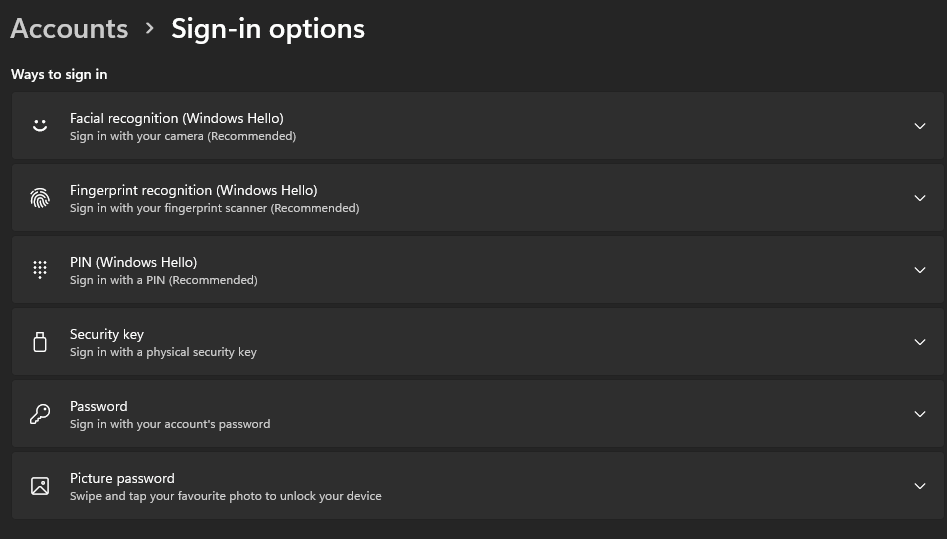
And we are selecting Security Key
Click Manage

Then you need to press the button on the side of the key and authenticate with your fingerprint
I can skip the next screen because I have configured the token via the app, but if you want to go direct, you can configure the fingerprint and PIN here
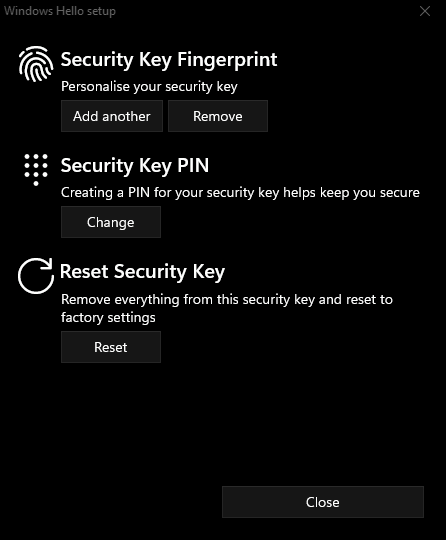
That’s Windows Hello all setup, to login, press the button on the side and authenticate with a fingerprint
M365 MFA
Now I want to secure my M365 environment
First go to this page (you may need to MFA if it’s already setup)
https://mysignins.microsoft.com/security-info
Click Add Sign-in method
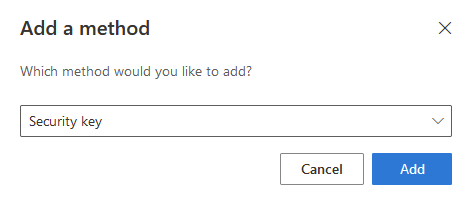
I’m using Bluetooth so select USB key, but if you are using a device with NFC, you can configure that way
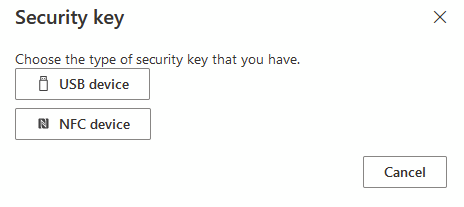
You will then get a few popups and a familiar screen to turn on and authenticate the device
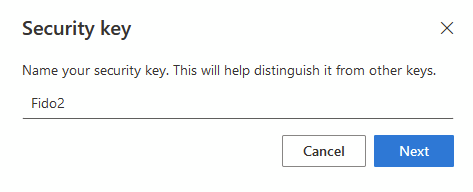
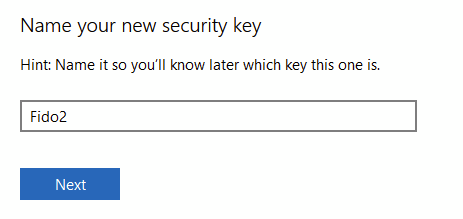
Once authenticated, give it a name
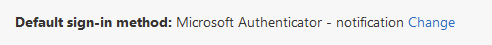
If you want, you can also click the Change text at the top to make this your default sign-in method (it’s listed as hardware token)
Azure
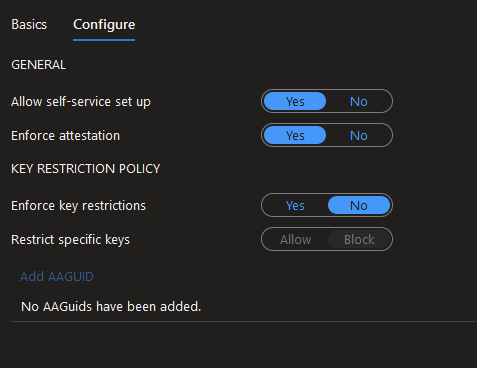
If you want to allow Fido2 auth for Azure AD objects, that can also be done by following this guide:
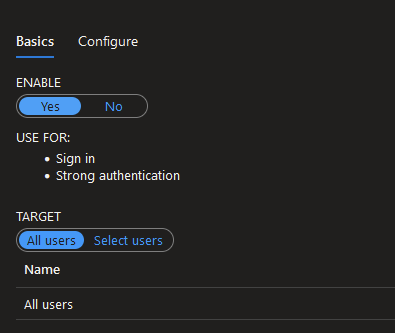
You can even restrict to particular token types if needed
We can also use the token to secure other services:
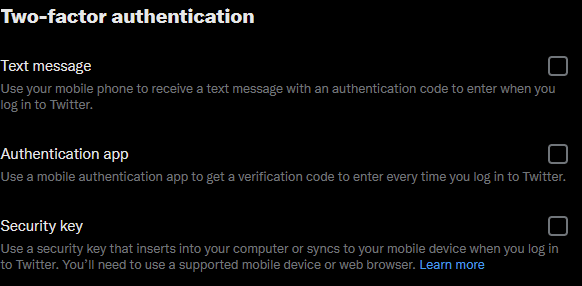
Navigate to this URL: https://twitter.com/settings/account/login_verification
Tick Security Key
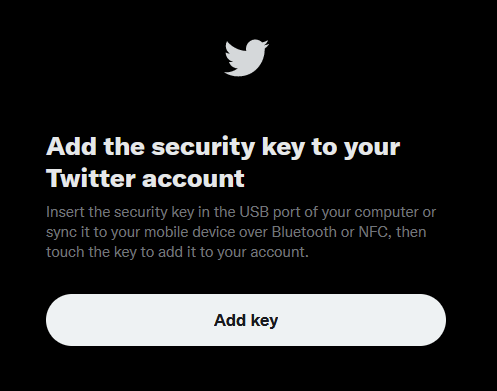
Add the key
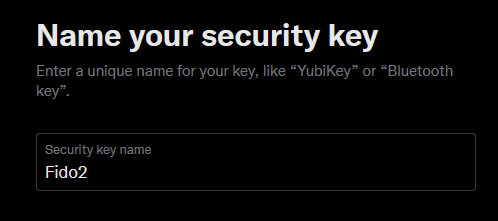
Again, you’ll have the standard Windows Security popups and then you’ll be prompted to name it:
As warned in the next popup, I would suggest adding another authentication method, if you lose the Fido2 token, break it, or it’s flat, you’ll be locked out!
You’ll also be given a backup code as a last resort, think of it as a break glass and store appropriately!
Gmail
To secure Gmail, navigate to this page: https://myaccount.google.com/signinoptions/two-step-verification/enroll-welcome?hl=en
Select Get Started and verify it’s you
Now we want to click Show more Options

And select Security Key
Click Next (unless you want to use key only)
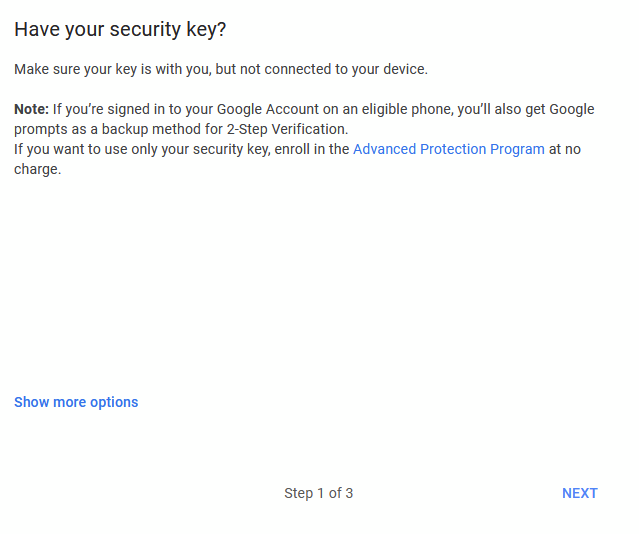
Then simply follow the same steps as we have used for the others
Again, you are given the option to save a backup key
Outlook.com accounts
I’m sure most people have a personal Outlook.com style account as well so we can also use it for MFA on there, or go one step further and passwordless:
Navigate to https://account.live.com/proofs/manage
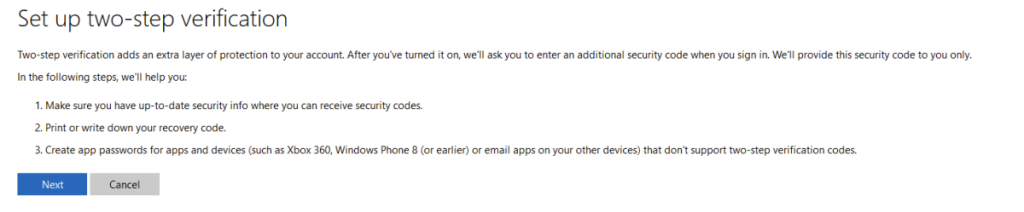
In Security click on Turn On MFA
Click Next
Like Twitter, you will be given a recovery code as a last resort, store it safely!
Now we want to add the device
Select Security Token
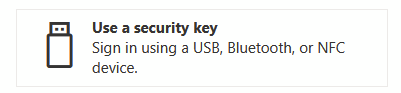
Again, Bluetooth is classed as USB
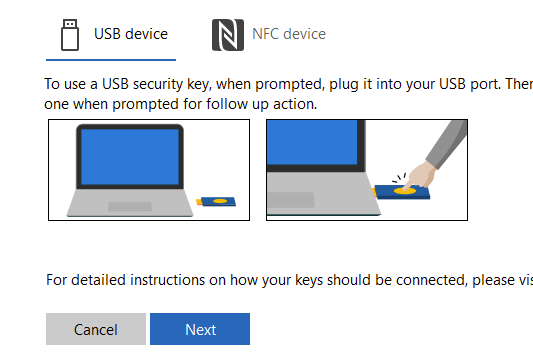
Follow the now-familiar steps and name the key
You can even go one step further and remove the password altogether, follow this guide for extra security
Hopefully you have found this useful, as always, comments are more than welcome!
