Windows Kiosks are a great idea and for public facing machines, work really well, especially in single app, Edge mode where in my experience it just works.
But what if you need something a bit more “internal”? The main issue with a single page Edge kiosk is by nature it runs Edge in “InPrivate” mode so be sure that all data is wiped when the End Session button is clicked.
This gives us issues with Conditional Access policies, even if it’s running from a compliant device, in InPrivate mode, the device details are not being passed to Entra (it’s private after all) so Conditional Access defaults to not-compliant and blocks it.
We can’t add an exclusion at the user level, it’s a kiosk device so the user isn’t usually in Entra (yes, you can configure this, but it’s less secure). We could do device based filtering on the PC names, but surely these devices need to be more secure, not poking holes through the security barrier.
Fortunately, there is a way to run Kiosk devices in Edge only mode, but with the full Edge experience so CA is also satisfied.
We can complete this by using Assigned Access, some fancy parameters on Edge launch and a Settings Catalog policy to lock down the URLs.
Assigned Access
First thing we need to do is configure our XML and use Assigned Access instead of the built-in Single App Kiosk options (which just don’t give us the flexibility we need)
Some credit for these next parts, Jon Towles has an excellent guide on kiosks with assigned access here and the hidden Edge commands from Eric Lawrence (the creator of Fiddler!) here
First step, create a custom OMA-URI policy with these values:
OMA-URI: ./Vendor/MSFT/AssignedAccess/Configuration
Data Type: XML File
Content (Downloadable here):
<?xml version="1.0" encoding="utf-8"?><AssignedAccessConfiguration xmlns="http://schemas.microsoft.com/AssignedAccess/2017/config" xmlns:rs5="http://schemas.microsoft.com/AssignedAccess/201810/config" xmlns:v4="http://schemas.microsoft.com/AssignedAccess/2021/config">
<Profiles> <Profile Id="{64f010ec-c145-4a16-941c-3c245f435d6a}"> <KioskModeApp v4:ClassicAppPath="%ProgramFiles(x86)%\Microsoft\Edge\Application\msedge.exe" v4:ClassicAppArguments="--enable-features=msEdgeDeleteBrowsingDataOnExit https://myapps.microsoft.com --no-first-run" /> <v4:BreakoutSequence Key="Ctrl+A" /> </Profile> </Profiles> <Configs> <Config> <AutoLogonAccount rs5:DisplayName="Edge Kiosk" /> <DefaultProfile Id="{64f010ec-c145-4a16-941c-3c245f435d6a}" /> </Config> </Configs></AssignedAccessConfiguration>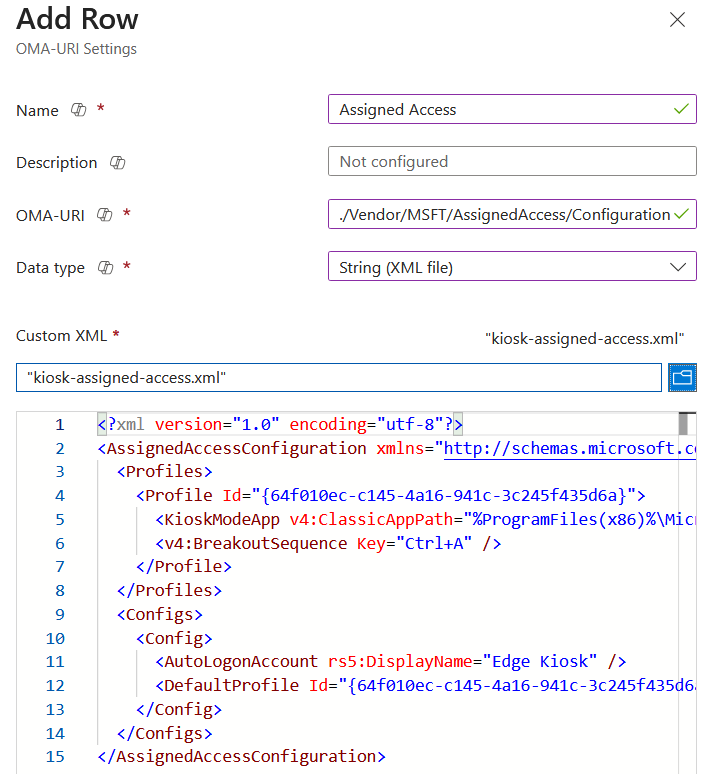
What we are doing here is changing the run command for Edge, removing any reference to Kiosk mode, setting the URL to use and using the fairly hidden classic app argument to delete all data when the browser is closed.
Settings Catalog
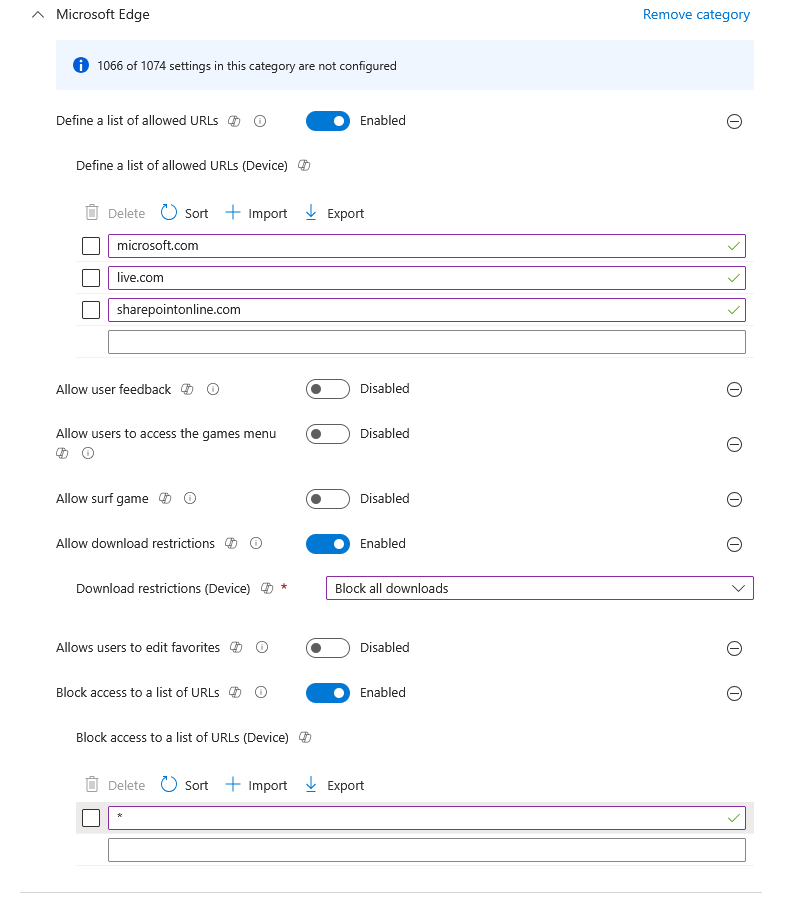
Whilst this is an internal device, unless the user has logged into a web app, there is zero auditing, so we need to make sure it can’t be used to browse any websites and for that we need a new Settings Catalog policy.
The two main settings we need here are:
Define a list of allowed URLs – Add the URLs for whatever website you are allowing. If it’s for M365 apps, they are all listed here
Block access to a list of URLs – Add “*” which blocks everything not in the allow list
I’ve also added some others which are probably not required, but nice to have anyway
Drawbacks and User Experience
There are two drawbacks of not using Kiosk mode:
- End session button isn’t present so users have to close the window (it auto reloads)
- You can’t set the timeout directly in the edge launch commands
The timeout can be sorted by pushing a scheduled task to the machine with PowerShell, you can grab a script to do so here
User experience is good, machine boots, signs-in and loads Edge. When the user closes Edge, everything is removed and it relaunches to a fresh window.
Hope this helps some of you!
