In the never-ending quest to make repeatable tasks easier, I’m taking on authentication to MS Graph and Azure AD
As I’m sure you’ve worked out by now, I like to let Powershell do the heavy lifting on most tasks and more recently, that has included spinning up new Intune environments, but I still have to authenticate when running the script which means I have to sit and watch it.
To solve this, I have created a new script to create App Registrations / Enterprise Apps / Service Principals which I can then pass through to any Intune / Azure / Azure AD scripts to authenticate for me.
Update 15/05/22 – The password parameter requires Powershell 6.1 so I have added script logic to stop execution if an older version is detected
As always, the script is on Github here
It’s a very repeatable task so it’s also on PowerShell Gallery to make it easier to install:
Install-Script -Name create-intuneappregistrationThis uses the AzureADPreview module which has increased functionality when assigning roles, but if you don’t have it, fear not, it will install in the user context.
The only input the script needs is two popup windows to authenticate against Azure, it grabs all other information.
MS Graph App Registration
First it creates an MS Graph App Registration called “Intune App Registration” with the following permissions:
- AppCatalog.ReadWrite.All
- Application.ReadWrite.All
- BitlockerKey.Read.All
- DeviceManagementApps.ReadWrite.All
- DeviceManagementConfiguration.ReadWrite.All
- DeviceManagementManagedDevices.ReadWrite.All
- DeviceManagementServiceConfig.ReadWrite.All
- WindowsUpdates.ReadWrite.All
- Policy.ReadWrite.ConditionalAccess
- User.ReadWrite.All
- Group.ReadWrite.All
- GroupMember.ReadWrite.All
- PrivilegedAccess.ReadWrite.AzureAD
- PrivilegedAccess.ReadWrite.AzureADGroup
- PrivilegedAccess.ReadWrite.AzureResources
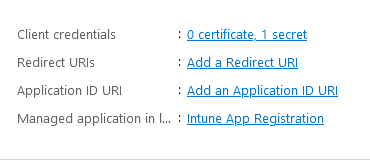
The App details (including secret) are stored and output in a CSV at the end
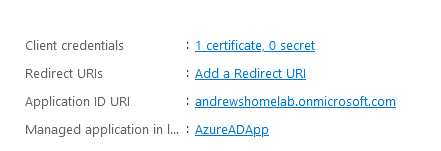
Azure AD App Registration
As the AzureAD commandlet requires a certificate to connect rather than a secret, the script creates a second App Registration called AzureAD App
It also creates a self-signed certificate with the DNS name to match your tenant domain and a randomly generated password on the exported pfx
This app has the following roles:
- User Administrator
- Privileged Access Administrator
- Conditional Access Administrator
Output
The script will create a folder at C:\AppRegistrations and a CSV file with the naming convention “tenantname-AppID-details.csv”
The CSV file contains:
- TenantID
- AppID
- EnterpriseAppID
- AppSecret
- GraphDisplayName
- TenantDomain
- CertPassword
- AzureADAppID
- AzureADAppName
- AzureADServicePrincipal
- AzureADClientID
Also in the folder you will find the PFX certificate for connecting later
Connecting to MS Graph and Azure AD
First we need to grab the details from the CSV.
I’m working on having multiple tenant details in the folder so use a wildcard to find the correct file:
##Get App Reg Details
$appregcsvpath = "C:\AppRegistrations\tenantdomain*.csv"
$appimport = (Get-ChildItem $appregcsvpath).FullName | import-csv
$certpath = "C:\AppRegistrations\*.pfx"
$pfxfile = (Get-ChildItem $certpath).FullName
##Your App Registration Details
$clientId = $appimport.AppID
$clientSecret = $appimport.AppSecret
$azuresp = $appimport.AzureADClientID
$certpassword = $appimport.CertPassword
$pwd = ConvertTo-SecureString -String $certpassword -Force -AsPlainTextNow we need to grab the certificate thumbprint:
$certdetails = get-pfxcertificate -file $pfxfile -password $pwd
$thumb = $certdetails.ThumbprintConnecting to MS Graph:
$tenant = $userUpn.Host
$authority = "https://login.windows.net/$tenant"
## Connect to MS Graph
Update-MSGraphEnvironment -AppId $clientId -Quiet
Update-MSGraphEnvironment -AuthUrl $authority -Quiet
Connect-MSGraph -ClientSecret $ClientSecret -QuietConnecting to Azure AD:
Connect-AzureAD -TenantId $csvtenantid -ApplicationId $azuresp -CertificateThumbprint $thumbThat’s it, of course you can re-use the App Registration for anything you are automating in Intune, environment backups, scripts to quickly grab details, anything.

Hi Andrew,
Were you already aware of that this line “$certdetails = get-pfxcertificate -file $pfxfile -password $pwd” is not working?
The -password paramater doesn’t exist. You can remove this paramater and then you receive a prompt to enter your cert password. But otherwise it won’t work.
Hi Roy,
Can you make sure you are running Powershell 6.1 or above please? The password parameter wasn’t in earlier versions:
https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.security/get-pfxcertificate?view=powershell-7.2
I will add some login into the script to it fails on older versions with a message to upgrade
Thanks for the feedback!
Andrew