Enrollment Limits and Restrictions are an excellent feature in both Azure AD and Intune, but they are always worth keeping an eye on before a user receives a new device and is greeted with a lovely error message.
Whilst you can log into Azure AD or Intune, count the devices assigned to a user (or enrolled by), check the AAD limit, check which AAD group they are in, check which policy the group is attached to (plus the priority if assigned to more than one), it’s all a bit long-winded.
Fortunately, this is all accessible via the amazing powers of Graph so I have put together a script to do the work for you.
As usual, you can get the script from PSGallery:
Install-Script -Name check-intune-user-enrollmentsOr from GitHub Here
In non-automated mode, simply authenticate to Graph and it will present a popup of users who are at or over either limit:
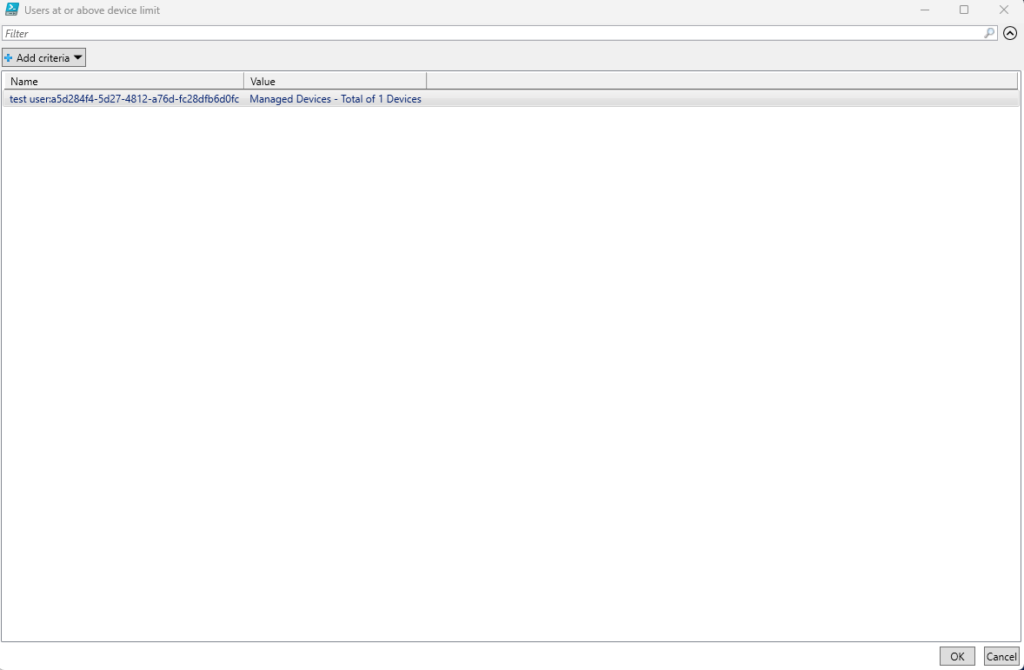
You can filter at the top for larger environments and it will show you which item is hitting the limit (Managed/Intune or Registered/AAD) as well as their total number of devices.
Selecting a user and clicking OK will give a list of their Registered and Intune Managed devices as well as the enrollment date and the date last seen as well as that users personal limits in the Title field:
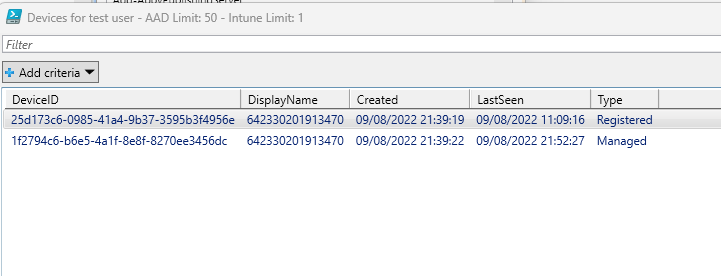
The script automatically checks the group memberships for the users and finds which Intune enrollment policies are applied to the groups. If multiple are detected, it finds the one with the highest priority.
To try and improve speed for larger environments, the initial Graph calls populate arrays which are then used later to grab the data.
Automation
Of course, as with most of my scripts, you can set this to run in an Automation account and email you the output.
Let’s start with the Automation Account within Azure
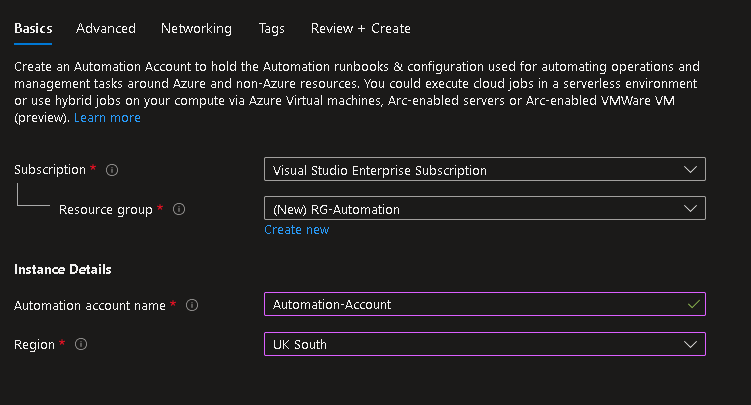
Once that’s complete we want to deploy the required modules to it
In PowerShell Gallery select these modules and deploy to Azure Automation:
NOTE: Make sure you select the non-preview version
https://www.powershellgallery.com/packages/Microsoft.Graph.Authentication/1.19.0
https://www.powershellgallery.com/packages/Microsoft.Graph.Users/1.19.0
Once deployed, we can reference them in our script
Next up, we need an AAD App Registration we can use to grab the backups
In Azure AD, create a new app registration:
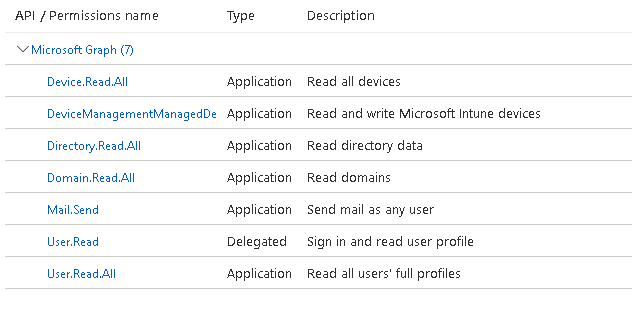
Within API Permissions grant these roles under MS Graph:
- User.Read.All
- Device.Read.All
- Domain.Read.All
- Directory.Read.All
- DeviceManagementManagedDevices.ReadWrite.All
- Mail.Send
You’ll note it’s still missing permissions so you now need to click the Grant Admin Consent button
Finally create a Secret and save that, the App ID and the Tenant details to use in the script
Now, back to the Azure Automation Account and click Runbook
Create a new Runbook
Now, back to the Azure Automation Account and click Runbook
Create a new Runbook
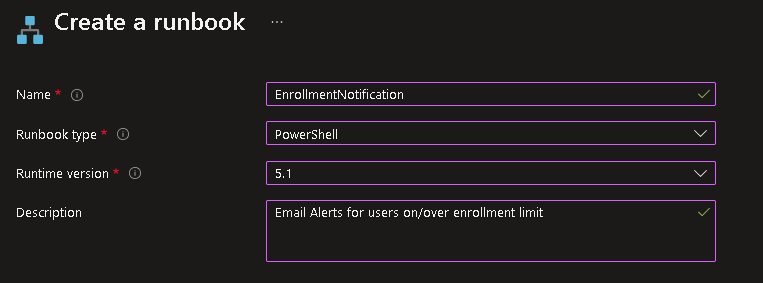
Now edit these variables in the script and add it:
##Set to Yes
$automated = "No"
##Your Azure Tenant ID
$tenantid = "<YOUR TENANT ID>"
##Your App Registration Details
$clientId = "<YOUR CLIENT ID>"
$clientSecret = "<YOUR CLIENT SECRET>"
$EmailAddress = "<YOUR EMAIL ADDRESS>"
##From Address
$MailSender = "<YOUR FROM ADDRESS>"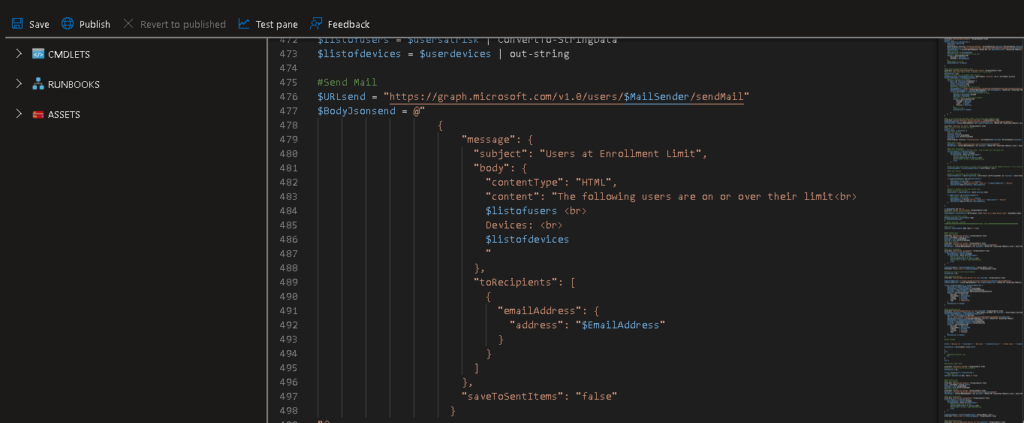
Click Test Pane to make sure it’s worked
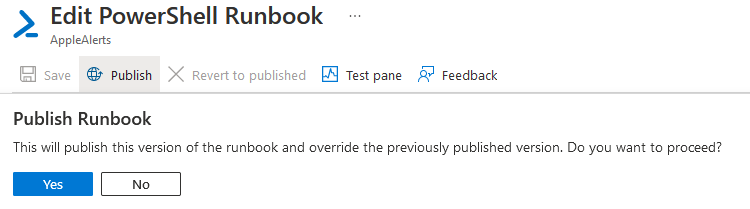
Now we need to publish it once it’s tested ok
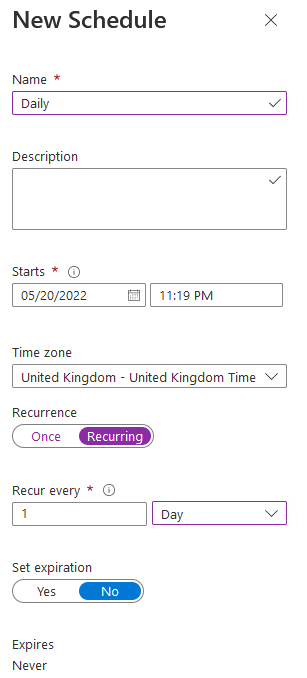
Now add a schedule to run it daily
That’s it, you’ll now get a nice email list each day to hopefully try and avoid additional support calls!

This is great, but not having any luck getting it to work. I should have perms etc and all modules loaded.
Installing Microsoft Graph modules if required (current user scope)
Microsoft Graph Authentication Already Installed
Microsoft Graph Users Already Installed
Connect-ToGraph : Cannot process argument transformation on parameter ‘Scopes’. Cannot convert value to type
System.String.
At C:\users\redacted\downloads\check-intune-user-enrollments.ps1:194 char:25
+ … aph -Scopes Device.Read.All, User.Read.All, Domain.Read.All, Director …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidData: (:) [Connect-ToGraph], ParameterBindingArgumentTransformationException
+ FullyQualifiedErrorId : ParameterArgumentTransformationError,Connect-ToGraph
I’m uploading a new version in the next few minutes which should fix it