I’m not writing a post covering Windows LAPS or how to set it up, there are many excellent articles out there which have you covered.
For this one, you can automate the setup, not only of the LAPS policy, but also creating a new local administrator on the device to use with it. It will even toggle the setting in AAD if you haven’t done so already!
The default configuration for Windows LAPS is to re-enable the default local admin (and you can also rename it), but the SID remains the same so fo extra security we will create a whole new user account.
And here is the new script. As usual you can find it on GitHub Here
Or on the PSGallery
Install-Script -Name configure-laps-intuneThis script can take an account name parameter at the command line, or if one isn’t passed, it defaults to “lapsadmin”.
Whilst LAPS will handle the password moving forward, we want it to be secure from the start so it generates a random 20-digit password to be extra careful.
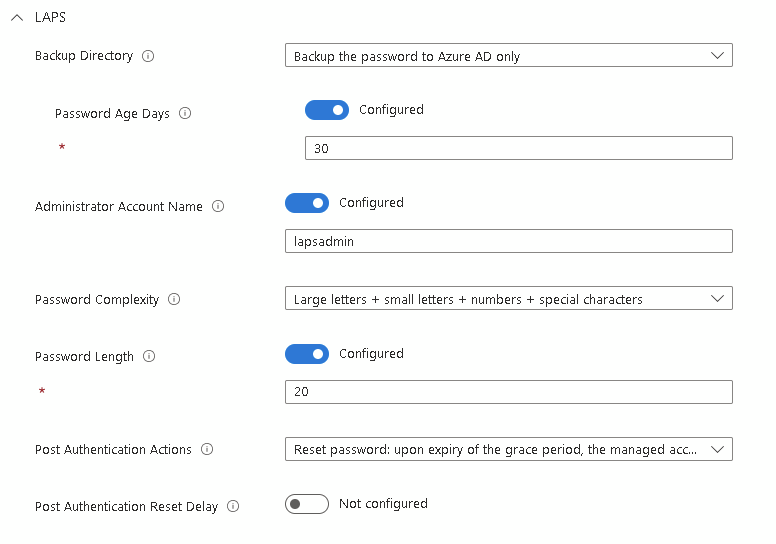
LAPS is then configured with these settings (the account name will match anything sent in the parameter)
Finally, it assigns both policies to All Devices

The description under Endpoint Security > Account Protection > LAPS Config incorrectly states lapsadmin even when a custom name is applied, same with the custom OMA-URI description.
I can see the issue, you need to replace lapsadmin with $accountname
I will get the script updated too
The main script has been updated now
Hi !
First of all, great job, it works perfectly !
Got a question though. I did launch the script by default using the PSGallery script, but didn’t not put any parameters, so it deployed with lapsadmin.
Is there a way/script to delete this local admin everywhere so i can launch it again with the account name i wanted ?
An other question, if someone “disappear” from intune device manager, (like he’s not connected for a long time, 1 year+), is it possible to recover his lapsadmin password somewhere ? Because the device is not listed anymore.
Thank you !
Hi,
You could use an account protection policy, or a remediation to remove the user (net use delete)
I dont think there is a way to find for old devices, you could check if the device still exists in Entra or Graph, but after a year that is a long shot.
Andrew, great script and I’ve used it with many different tenants. Ran into an issue with one of the tenants I manage where the systems don’t seem to be getting either the LAPS or Account creation policy. No errors and the policies have been in place over a week. Systems are checking in to Intune every day. Any ideas on what or where to check? The systems lapsadmin account has not been created at this time. Thanks.
Hi, The first thing is to check in Entra and see if LAPS has been enabled centrally.
Go to Devices – Overview – Device settings and look for:
Enable Microsoft Entra Local Administrator Password Solution (LAPS)
The setting is on. This is making me crazy. Does the machines being Hybrid AAD Joined make any difference?
You are a mad genius. Thank you.
How to mod/cut off the script only to create the local admin user and to assign it to the administrators group?
The reason: I already have LAPS enabled in intune and it works. Need a unified admin account on all intune joined windows devices because currently the intune laps policy applies only to devices that already have that particular admin account and ignores the rest of the devices.
Thank you in advance.
Glad it’s useful. Remove line 260-399 and it will only do the account creation.
Then amend the JSON for line 243 to point to a group ID
My fault, I didn’t switch allDevicesAssignmentTarget for groupAssignmentTarget… It worked like a charm!
Thanks again for sharing your knowledge!
It seems that “microsoft.graph.groupAssignmentTarget” does not have such a property (groupID):
“The property ‘groupId’ does not exist on type ‘microsoft.management.services.api.allDevicesAssignmentTarget’.”
Maybe be another microsoft.graph.XXX data type?
Can you share the full assignment JSON?
Hi again Andrew,
sorry but I am not into Graph, Let’s say my group is “AADJ-Devices”, what line should I change?
$lapsassignjson = @”
{
“assignments”: [
{
“target”: {
“@odata.type”: “#microsoft.graph.allDevicesAssignmentTarget”
}
}
]
}
“@
You need this:
“target”: {
“@odata.type”: “#microsoft.graph.groupAssignmentTarget”,
“groupId”: “XXX”
}
But substiture the XXX for the Group ID (not the name)
Hi Andrew. How could we assign this policy to a specific group? Thanks for all your work!
Hi Alfonso,
You need to change the JSON from line 385 and swap it for a group assignment instead (remember it needs to be the Group ID, not the name)
Hi. Not working for me. Should it prompt for username and password?
Am I missing something?
Hi, what isn’t working? When you run the script it should authenticate to graph and create the policies in Intune
Thank you again. I have installed but seeing errors on the devices it’s being pushed to: -2016281112, though when i look at the devices, the new user is there and in the administrators group on the system. Also not seeing the password in Intune. Anything I should be looking for? I’m missing?
Setting name
Setting status
Error code
Password [./Device/Vendor/MSFT/Accounts/Users/mediadmin/Password]
Error
-2016281112
LocalUserGroup [./Device/Vendor/MSFT/Accounts/Users/m1admin/LocalUserGroup]
Error
-2016281112
That policy will error out after the first run as it is setting a password which LAPS is then capturing. Are any devices reporting back in LAPS?
Thank you. Does it need to be a workstation or can it be a server?
Anything will work, it will automatically install the powershell modules. I’ve never tested it on macOS or Linux though so can’t be sure about those
Do I have to run it on each machine in the environment or just one machine and it will do the rest of the systems? Trying to implement LAPS in an AAD environment with a new local admin.
Just run the script once from a machine and login with an Intune Admin or Global admin account when prompted. That will create the policies for you
New to Intune as well, how is the automation of this achieved? run it in Intune under Devices > Scripts?
Hi, This one you just run on your own machine and it deploys everything into Intune for you
Thank you. FYI typo on line 77 (wirte-host)
Thank you, I’d missed that. Updated now 🙂
Sorry, a little dense today. I’ll run this PS once from my workstation and then it handles the rest? Or packaging this as a Win32 app to deploy as an app in Intune.
Just run it from your machine and it will sort it all for you 🙂
Hello Andrew,
I have enabled it in the Azure tenant and then created the policy, however getting error “rotateLocalAdminPassword Failed” any idea?
I have checked for other conflicting policies and disabled any that could be.
I have an account created with that name.
I have re-created the policy and left it with the default admin account to see if that works.
all to no avail.
Hi Danny,
Did the account create correctly? Do you have any old on-prem LAPS setup?
Sorry one further question. Will this setting automatically apply to any future devices that are connected to our Azure AD
Yes, it is targeting all devices so as soon as they are enrolled into Intune, the policy will apply
Perfect, thank you for your help and quick reply.
Hi Andrew,
Firstly thank you for this article & script.
Please excuse my ignorance, as I am new to this, but once it password has been randomly selected, where would I be able to find the password when I need to log in with the local admin account?
Thank you
Hi,
If you look at the Device details in Intune there is a new menu item called “Local Admin Password”. That will display the password for you.
You can also access it through Azure AD Devices as well if you would prefer
Hope this helps
Hello Andrew, thanks for the script.
Glad you’re finding it useful!
Appreciate you always looking under the hood right away, thank you for the information!
Glad you find it useful, first place I look when these are released is what’s going on in Graph 🙂