As I am sure you have noticed, the Get-WindowsAutoPilotInfo script and associated WindowsAutoPilotIntune module have been updated and whether you are using the official one, or my forked version, the authentication method has changed to the Microsoft.Graph SDK.
In this post we will look at the two different authentication methods and the permissions required:
User Authentication
This uses the Connect-MgGraph command with the following scopes:
Group.ReadWrite.All
Device.ReadWrite.All
DeviceManagementManagedDevices.ReadWrite.All
DeviceManagementServiceConfig.ReadWrite.All
GroupMember.ReadWrite.All
DeviceManagementScripts.ReadWrite.AllThese are required so you are covered if you also use the “-group” parameter to add devices to an Azure AD Group.
We then run this command to do a basic online enrollment
get-windowsautopilotinfo.ps1 -onlineYou’ll be prompted to login to your tenant:
Microsoft Graph Command Line Tools (it may be listed as Microsoft Graph PowerShell on some tenants) which are used by the SDK to run commands needs to setup an Application within your Azure Active Directory with the permissions selected earlier:
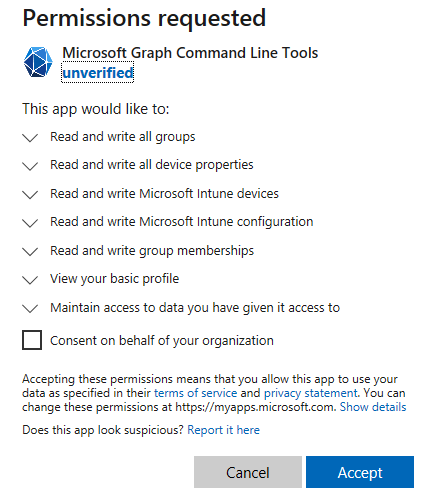
We will start by looking at what happens if the box is left unticked:
If we navigate to Azure AD and click on Enterprise Applications, we can see the app in there:
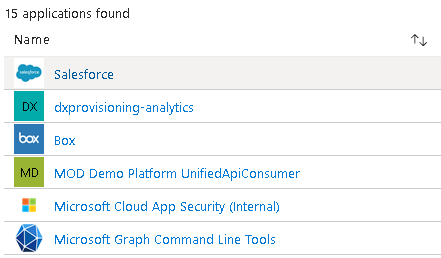
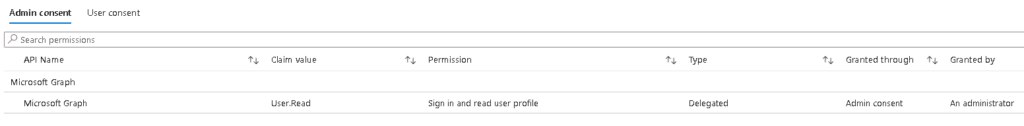
Clicking on that and then permissions, nothing has been given admin consent:
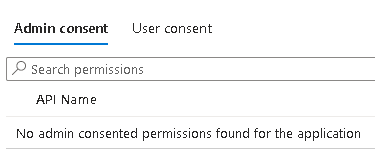
But we can see those permissions under user consent with one user added:
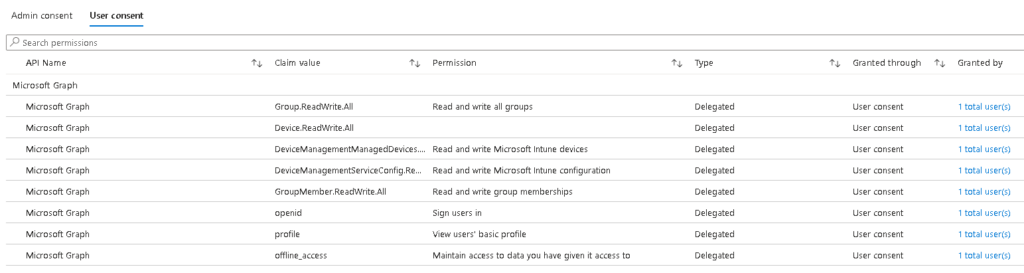
In here we can click the big blue button to consent permissions to everyone in the tenant:

Clicking this will prompt you to sign in with a global admin, but this only adds permissions to view the current user which is no use to us:
So what happens if we tick the box?
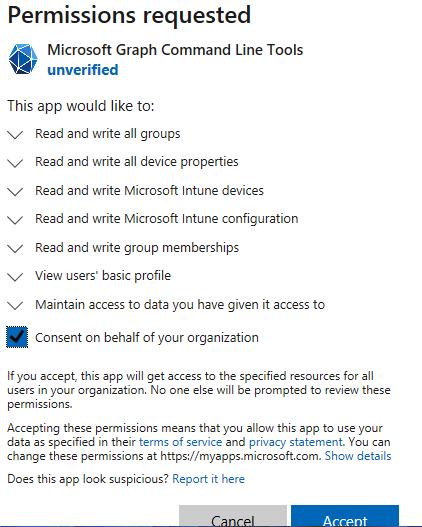
Now in the enterprise app, the permissions are greyed out so in theory anyone can run the script. That’s worth testing. After logging in with a different user, all worked as expected, no prompt to set permissions.
Connecting to WindowsAutoPilotIntune Module
When using this module, you first need to connect to Graph, use this command:
Connect-MgGraph -scopes "Group.ReadWrite.All, Device.ReadWrite.All, DeviceManagementManagedDevices.ReadWrite.All, DeviceManagementServiceConfig.ReadWrite.All, GroupMember.ReadWrite.All"Connecting with an App Reg
The other option for connecting is using an application registration where an Application ID and Secret is supplied to the script to use instead of user credentials.
Let’s start by creating a new app reg:
Within Azure AD, click App Registrations and then New registration:
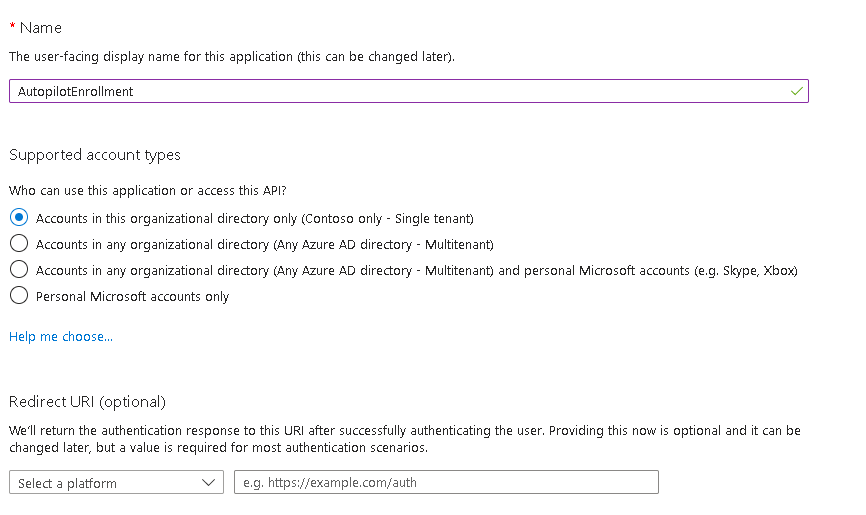
Single tenant is fine and we’ll set the redirect UI in a minute
Make a note of the client ID and click Add Redirect URI

Click Add a platform

Select Mobile and Desktop Applications
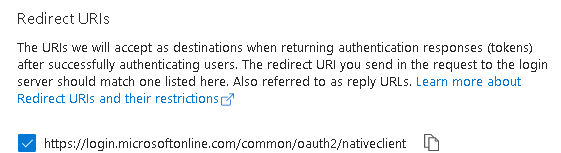
Select the top URI
Now click API permissions
Add a permission

Select Microsoft Graph
We want to use Application Permissions so no user is required
Add the permissions mentioned earlier:
Group.ReadWrite.All
Device.ReadWrite.All
DeviceManagementManagedDevices.ReadWrite.All
DeviceManagementServiceConfig.ReadWrite.All
GroupMember.ReadWrite.AllYou will notice they have added, but do not have admin consent:
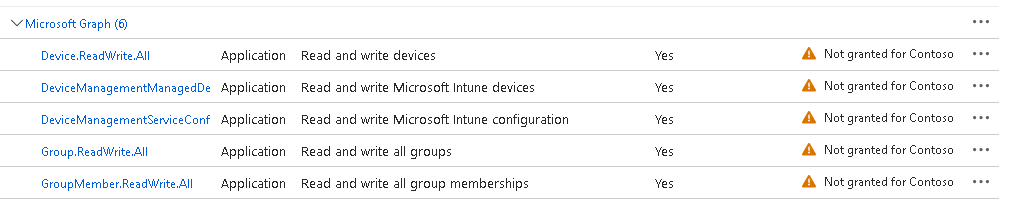
Click the Grant admin consent button

Now the last thing is we need a secret (think of it as the password)
Navigate to certificates and secrets
Click new client secret
Make a note of the secret value, you can’t view it again afterwards so will need to create a new secret

Now to use this with the script (obviously replace 12345 with your values):
get-windowsautopilotinfo.ps1 -online -TenantID 12345 -appid 12345 -appsecret 12345Troubleshooting
A special thanks to Kenny Renström for help with these!
-
- “The provided access token has expired” – Check the system date/time are correct
-
- If using an app secret, make sure your redirect URIs are set correctly (the top option in Mobile and desktop applications will be sufficient) Link
-
- “Invoke-autopilotsync: Microsoft.Graph.Powershell.Authentication.Helpers.httpresponseException: Response status code does not indicate success: Conflict” – The sync has been run too many times, wait 10 minutes and re-run the script (I am also fixing this in the code itself)

Andrew,
Thanks for this guide – used it in the past with great success. I setup an App Registration and used this method to enroll hundreds of machines into our Autopilot.
All of a sudden, I’m getting the connect-mggraph error that the access token has expired. First thought was that date/time was off on the device – but that was not the case. My client secret is not expired. I even went so far as to completely rebuild my App Registration from scratch – but still getting the same error.
Any thoughts on this?
Thanks!
Matt
Hi Matt, that can happen if the Redirect URI isn’t set on the app reg. Can you see if you get the same issue on the community version as well
I do have a Mobile and desktop application platform Redirect URI configured, https://login.microsoftonline.com/common/oauth2/nativeclient
I haven’t tried the community version – but I’ll give that a go shortly.
Thanks!
Interestingly – this started working again today with no changes on my end. Guess I will chalk this up to some kind of transient issue on Microsoft’s end. Thanks for your time all the same.
I am getting this error:
Add-AutopilotImportedDevice : System.Management.Automation.ValidationMetadataException: The cmdlet cannot run because Authentication is set to Default and Connect-MgGraph was not called. Invoke ‘Connect-MgGraph’ or specify Authentication to be ‘UserProvidedToken’ and Provide a Token then retry
Have you connected to Graph first (if not using an app-reg)? I would suggest looking at the community script as well which includes the connection amongst other improvements
Thanks for the reply, I’m connecting using an app-reg – I actually missed the first error which is probably the cause of the issue ‘unable to decode the header’. Have you seen this before?
Get-WindowsAutoPilotInfo.ps1 -Online -TenantID xxx -AppId xxx -AppSecret xxx
Connect-MgGraph : IDX12729: Unable to decode the header ‘[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.%5D‘ as Base64Url encoded string. jwtEncodedString: ‘[PII is hidden. For more details, see
https://aka.ms/IdentityModel/PII.%5D‘.
At C:\Program Files\WindowsPowerShell\Modules\WindowsAutopilotIntune\5.7\WindowsAutoPilotIntune.psm1:62 char:9
+ Connect-MgGraph -AccessToken $secureToken
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Connect-MgGraph], ArgumentException
+ FullyQualifiedErrorId : Microsoft.Graph.PowerShell.Authentication.Cmdlets.ConnectMgGraph
Connected to Intune tenant xxx using app-based authentication (Azure AD authentication not supported)
Gathered details for device with serial number: xxxxxx
Add-AutopilotImportedDevice : System.Management.Automation.ValidationMetadataException: The cmdlet cannot run because Authentication is set to Default and Connect-MgGraph was not called. Invoke ‘Connect-MgGraph’ or specify
Authentication to be ‘UserProvidedToken’ and Provide a Token then retry
at System.Management.Automation.MshCommandRuntime.ThrowTerminatingError(ErrorRecord errorRecord)
At C:\Program Files\WindowsPowerShell\Scripts\Get-WindowsAutoPilotInfo.ps1:346 char:17
+ … imported += Add-AutopilotImportedDevice -serialNumber $_.’Device Seri …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Write-Error], WriteErrorException
+ FullyQualifiedErrorId : Microsoft.PowerShell.Commands.WriteErrorException,Add-AutopilotImportedDevice
Sorry for what might be a stupid question, but I’ve installed the community script using
Install-Module -Name WindowsAutopilotIntuneCommunity -AllowClobber
How do I actually connect using the community script?
Thanks again
That’s not an error I’ve seen before.
With the community one, it will auto-connect when you run it
I get this error now. using app-based (Azure AD authentication not supported)
Try the community script instead, I think the official one has a deprecated module in it
Here is the uput from the script:
Add-AutopilotImportedDevice: C:\Program Files\WindowsPowerShell\Scripts\Get-WindowsAutoPilotInfo.ps1:346
Line |
346 | … imported += Add-AutopilotImportedDevice -serialNumber $_.’Device Seri …
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| Response status code does not indicate success: Unauthorized (Unauthorized).
That should need: DeviceManagementServiceConfig.ReadWrite.All
It might be worth trying the community version of the script as well in case there has been a change to the official one
I followed the guide to set up the app and I am getting this error when running the the script Response status code does not indicate sucess: Unauthorized (Unauthorized)
Do you have ny idea what could be the issue?
That normally means one of the permissions is missing
The permissions listed in guide are the ones added would there be a need any other ones potentially?
There shouldn’t be, does it tell you the URL with the unauthorized error? Are the permissions Application and not Delegated?
Any updates on this? I keep getting the same error when it tries to run `Get-AutoPilotDevice`
Check you app reg permissions, try the community version as well
Quick question related to the module.
I’m using version 5.6 and connect via app reg.
I get the following error when using Set-AutopilotDevice :
Response status code does not indicate success: NotFound (Not Found)
App reg has the permissions mentionned in this article.
Get-AutopilotDevice works fine.
Any idea?
Can you try the community versions and see if they work any better?
I found the problem and will work on an appropriate solution.
Basically, my script creates a user in Entra and eventually assign a device to said user, but he is not yet visible by Autopilot (?) so this is why Set-AutopilotDevice fails.
Not sure if forcing a sync between Intune and Autopilot would work, but I’ll try a few different things.
Hi Andrew,
All is working with the script and we are able to add devices to an online environment. But with setting the permissions needed for the app registration to work we are also able to delete devices with that app registration. So if someone comes along, looks at the script and figures out how to login to Microsoft Graph using the app credentials they are able to delete stuff. Is there a way to deny the delete permissions and to only add to the environment?
Hi,
As it’s a read/write all permission you can’t be any more specific with it unfortunately. Your only other option would be to use an automation with a web hook so they can’t access the script at all, but that would take a fair bit more coding.
Hi, Andrew
When running the script, i’m getting an error when running with the “-group” parameter. “New-MgGroupMember : Insufficient privileges to complete the operation.” The device does enroll in autopilot and show in AAD and is assigned to the right group. I have granted the permissions you have listed above to the app registration. Is there something I’m missing?
Thanks
Hi,
The permissions should be Group.ReadWrite.All and GroupMember.ReadWrite.All for that part. Can you check they are added to the app reg and approved for the tenant?
Yes. Those permissions are added and approved.
Hi Andrew,
I have a question you may be able to answer. Around 4 months ago, we provided admin consent for the user auth for entire tenant to MS Graph Command line tools. It has just re-requested the auth again, would you know why it’s asking to re-authenticate? As the IT admins that are enrolling the devices do not have GA, they have to request us to grant admin consent again.
Hi,
Have you changed any permissions in the graph connection? Adding or removing a permission will prompt a full re-authentication.
It might be worth checking your Enterprise apps within Entra as well in case it has created a new one
Also, when devices was added to AAD portal, it was shown as disabled.
It sounds like either the Autopilot Profile or ESP page (or both) haven’t assigned to that device. How do you have them both configured for assignment?
No, I don’t get the login screen. The device shows in AAD portal as AAD joined and has the AutoPilot logo. The hostname is wrong and it’s the device SN as the hostname.
When I run dsregcmd /status it doesn’t show it being AAD joined.
Thanks for the great tutorial.
I have an issue though. When I run the script, the device gets Azure AD joined, but not intune joined. I do it through the OOBE though. Do you happen to know why that is?
Thank you so much!
Hi,
Do you get the OOBE Autopilot login screen? Do you have your Autopilot profile and ESP assigned correctly?
It’s also worth checking your MDM scope is set correctly in Entra
this works perfectly, thanks was going a bit crazy there for a while wondering why my original script wasn’t working but this online is so much easier thanks andrew.
Glad it’s working well 🙂
Hi Andrew,
Thank you for this post.
Setting up App Reg work for me but still having issues with User Auth.
I keep getting the following error:
Add-AutopilotImportedDevice: Microsoft.Graph.PowerShell.Authentication.Helpers.HttpsResponseException: Response Status codes does not indicate success: Forbidden (Forbidden)
GA role works, but want to give a role that is not GA and having trouble figuring that out.
Hi,
When you approved the original connection, did you tick the box to allow across the tenant? It should create an enterprise application with the required permissions
I certainly will! We have a good 1000+ devices to join this coming summer break so will be hammering AutoPilot daily! I’ve built you suggestion into a Powershell script to completely automate the process with minimal touch from our guys on the ground. If you’d like a copy let me know also.
Hi, I would love to have a copy of your automation if you wouldn’t mind. Cheers. julianddavidson # gmail # com
Which automation?
A…..Maze…..Ing!
I’ve been struggling with using credential auth; why bother just use your app-based method, and its even less for the guys on the ground to have to enter into the PC!
You Rock!
Glad you have found it useful 🙂
If there are any improvements you think would be useful to the script, please let me know!
Should I use the Get-WindowsAutopilotInfoCommunity.ps1 latest version or version 1.0? I’m asking it because I installed the Install-Module -Name WindowsAutopilotIntuneCommunity today but when I tried to run the get-windowsautopilotcommunity -Online -TenantID xxxxxx -AppID yyyyy -Appsecret wwwww but I’m facing an error like this:
Connect-ToGraph: cannot find a parameter that matches the name TenantID
Thank you for your support
Grab the latest community version, 3.1. That fixes the issue.
The official one will fail with the 2.0 graph modules
Unfortunately when I use the get-windowsautopilotinfo -Online -TenantId xxxxxxx -AppId xxxxxx -AppSecret xxxxxx I get an error that is not possible to convert Syestem.String do System.Security.String. Maybe there is some error on module when connecting to GraphApp
Are you using the community one? Get-WindowsAutopilotInfoCommunity.ps1
I was in a world of pain. Could not figure out why the prompted logon failed. All I could see was this diamond logo and that I did not have sufficient credentials. Now everything works again. Thanks to this informative, spot on advise post. Thanks for sharing.
That might be it, great! 🙂
Yes, GA account.
It may be the Graph PowerShell one you need, I think it has been recently renamed. My new tenant is “Command Line Tools” but my old one is “Graph PowerShell”.
I’ll update the post 🙂
Hi,
At the first step “We will start by looking at what happens if the box is left unticked:
If we navigate to Azure AD and click on Enterprise Applications, we can see the app in there”
I don’t have the `” Microsoft Graph Command Line Tools ” entry available within Enterprise apps. I’ve only the “Microsoft Graph Powershell” and “Graph Explorer” available.
What am I doing wrong?
Are you running with permissions to create the application in your tenant?