If you have ever used the original GitHub selection of PowerShell Intune Samples from Microsoft at the URL below, it will have included a hard-coded application registration (multi-tenant) which will be removed from the Microsoft tenant on 1st April and at that point your scripts will stop working.
https://github.com/microsoftgraph/powershell-intune-samples
How do I know if I will have issues?
Look within Entra ID, under Identity – Applications – Enterprise Applications
The app reg will be called Microsoft Intune Powershell with the client ID:
d1ddf0e4-d672-4dae-b554-9d5bdfd93547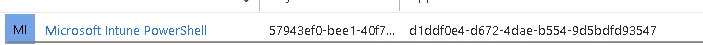
I have the app reg, what now?
The first thing to do is to look at any Intune scripts you are running and look for $clientID:
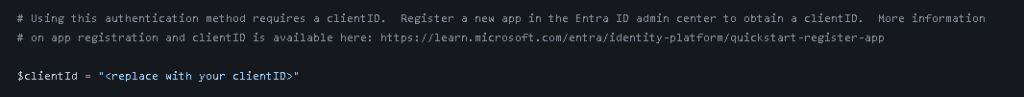
You now have two options:
- Create a new app reg within Entra, assign it the correct permissions and update the client ID in the script
- Use this opportunity to update your scripts.
These scripts are now showing their age and also use the AzureAD module for authentication which is also due to be deprecated this year so this may be a good time to review your scripts and switch to the Microsoft Graph SDK module instead. You can then use “connect-mggraph” for connection and replace “invoke-restmethod” with “invoke-mggraphrequest”.
There are also a selection of new scripts available directly from Microsoft at the URL below which use the SDK for authentication and requests
https://aka.ms/Intune/Scripts-blog
This may seem daunting, feel free to get in touch if you have any queries or need some guidance!

We would like to replace Connect-AzAccount -identity with connect-mggraph -identity but we use Keyvault and impossible (from what I know) to read keyvault with the new mggraph command when we connect with Identity.
You would need to mix them, grab the cert using AzAccount and use that in Graph.
If it’s within a runbook, you can assign a role to the managed identity and use that to auth