I have been fortunate enough to have been running Microsoft Security Copilot along with the new “Explorer” functionality for a while now so thought I would put it to the test to see how much of my everyday tasks as an Intune admin it can help me with.
If you have yet to get Microsoft Security Copilot configured in your tenant, I would recommend checking out this post from Joery which covers it from start to finish:
UPDATE – Intune plugin in Copilot for security (Public Preview)
Don’t forget when dealing with AI that RBAC is critical, last thing you want is people accessing data they shouldn’t be able to. Fortunately Mattias covers RBAC for Security Copilot here:
RBAC in Microsoft Security Copilot: How to Set It Up and Why It Matters
Before I dig into the good stuff, lets address the elephant in the room. As with all AI, it isn’t free to use and to some the cost may be a blocker, but before making that decision, have a look at how it can help and work out how many hours a week that will save you. Multiply that by 4 and that is the number of hours per month you will be saving, now compare that to the cost per month and decide if your time is worth that much (then make the same argument to your budget holder).
In this post I will be looking at the functionality within most of Intune, but not covering KQL and device query, to learn more about that, I’ll let the KQL expert do a better job here from Ugur
https://ugurkoc.de/kql-queries-made-easy-my-intune-admin-journey-with-copilot/
Using Microsoft Security Copilot
Before digging into the new Explorer functionality, lets see what is availalble in the existing Microsoft Security Copilot functionality within the Intune portal.
At a high level, it lets you summarize devices and policies to get an idea of exactly what is happening.
For policies, clicking on a policy gives the “Summarize with Copilot” button:

It then describes in plain English exactly what the policy is doing
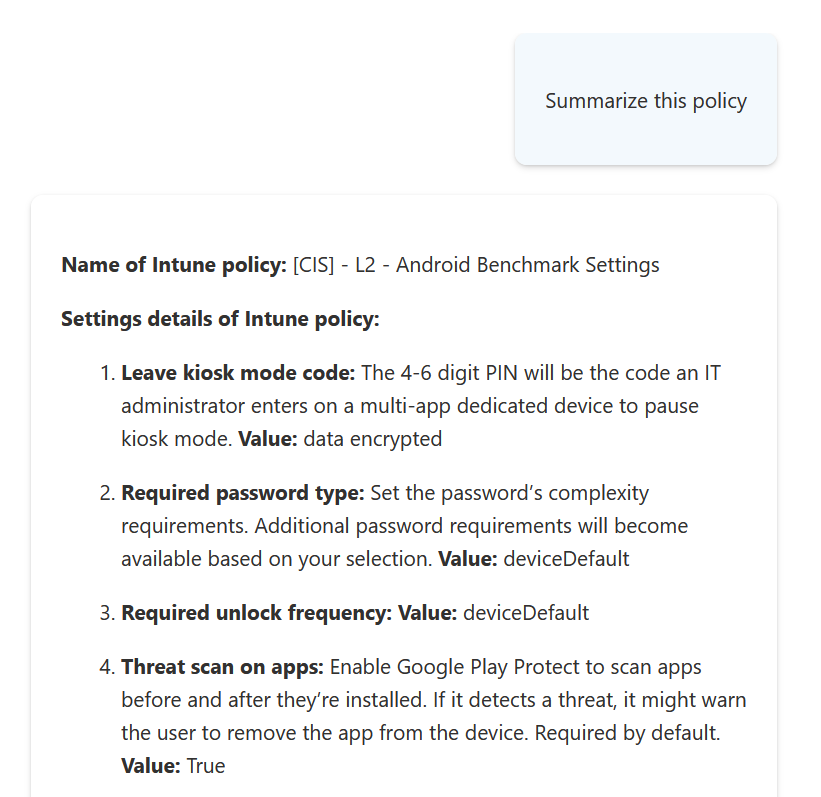
You can also follow-up with information about the impact the policy will have:
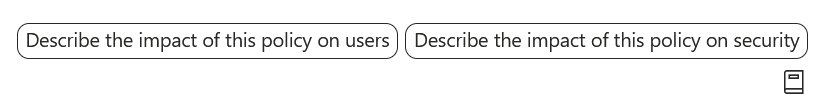
These will help please both your security department, but more importantly prepare for any user related queries and complaints after turning it on. You could even give your Service Desk staff access to Copilot to find this our for themselves.
We all know documenting is a chore, this certainly takes away one aspect of it

Looking within a policy itself, you can also summarize individual items by clicking the Copilot icon:
This gives a run-through of the setting, but also some useful follow-on prompts at the bottom to again check for user impact, but more useful, check if there is a recommended setting
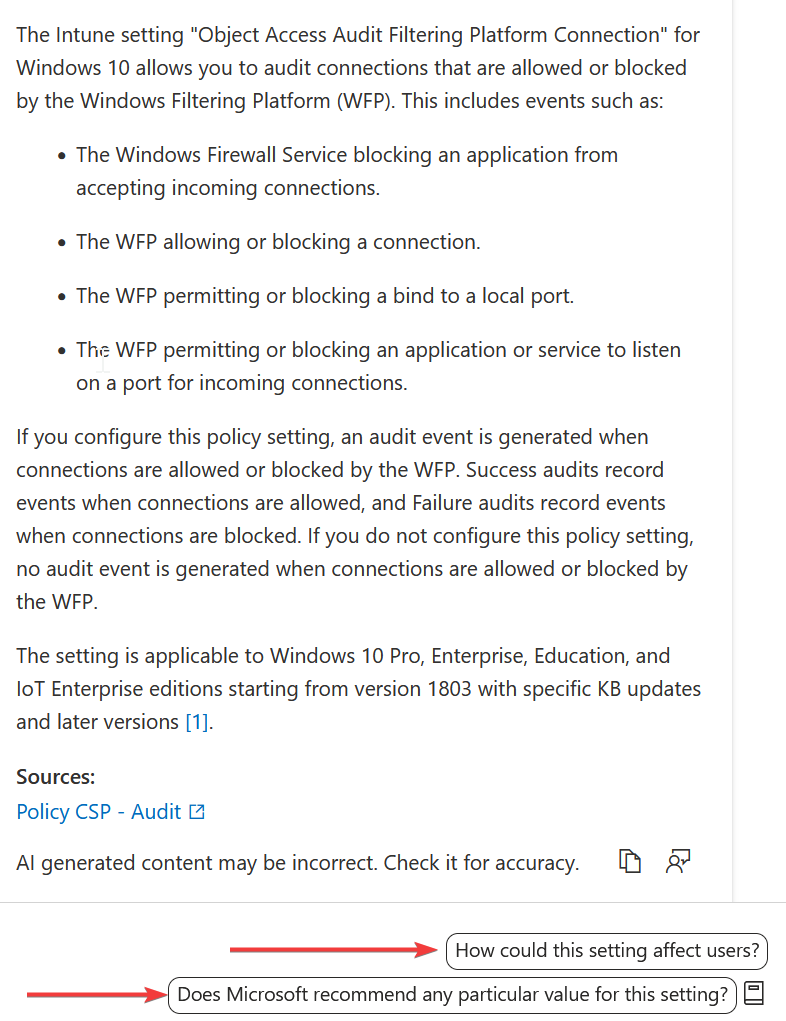
I’ve switched to a Bitlocker policy for this one because there is a recommended value, but this is invaluable for those just getting started who aren’t sure what is best
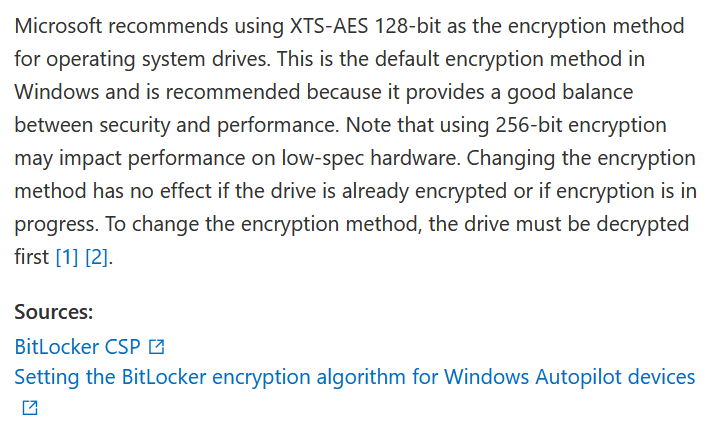
Annoyingly, this button only appears AFTER policy creation so you would need to guess it, create a policy (DON’T ASSIGN IT), then check your settings and fix.
If we switch to the device level, we have the same Summarize with Copilot button, but on clicking it, rather than just creating a summary, it gives some options to pick from. An important thing on all Copilot screens, there is a little book icon at the bottom which will help guide you when dealing with the prompts
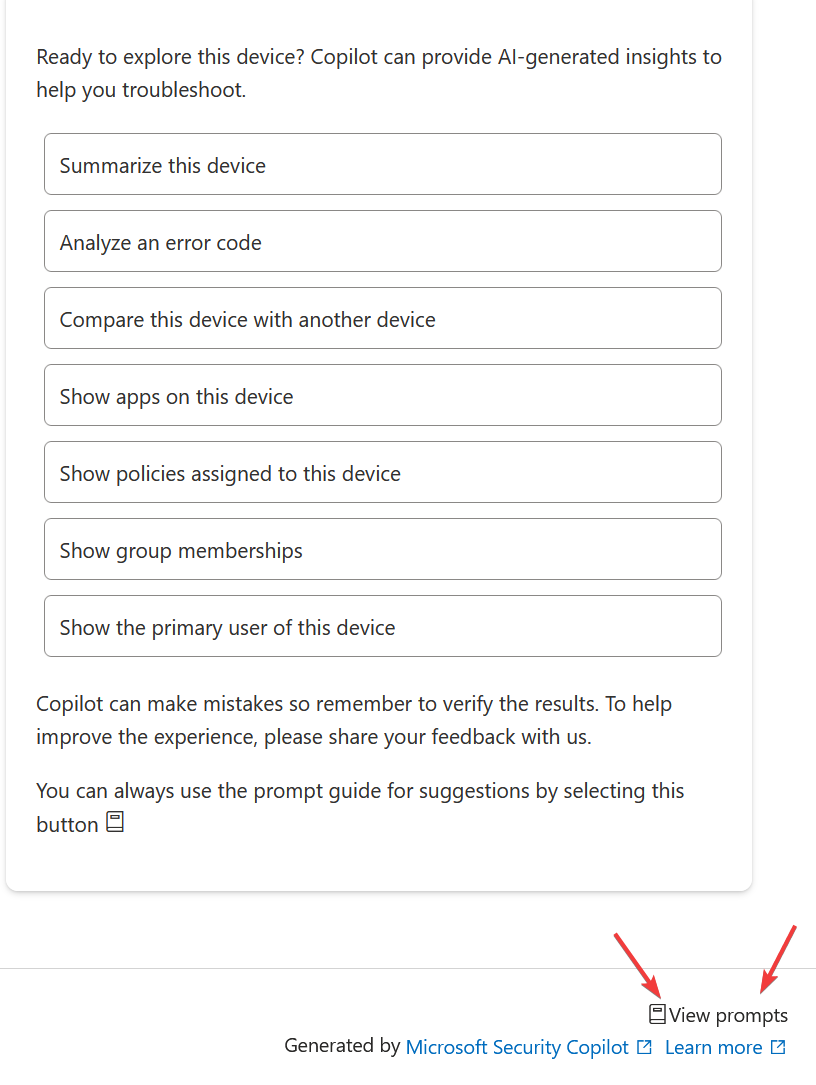
Some of these options are more useful than others:
- Summarize this device – This gives Object ID (always useful), compliance state (per policy), device group membership, the primary user and the last logged on user. Usefulness: 7/10
- Analyze an error code – This first asks you to enter the error code so for testing, I used the common 65000 error which helpfully said it wasn’t included in any Microsoft documentation so I tried again with “0x87d1fde8” which did at least bring back a result, but it wasn’t exactly useful. Usefulness: 2/10
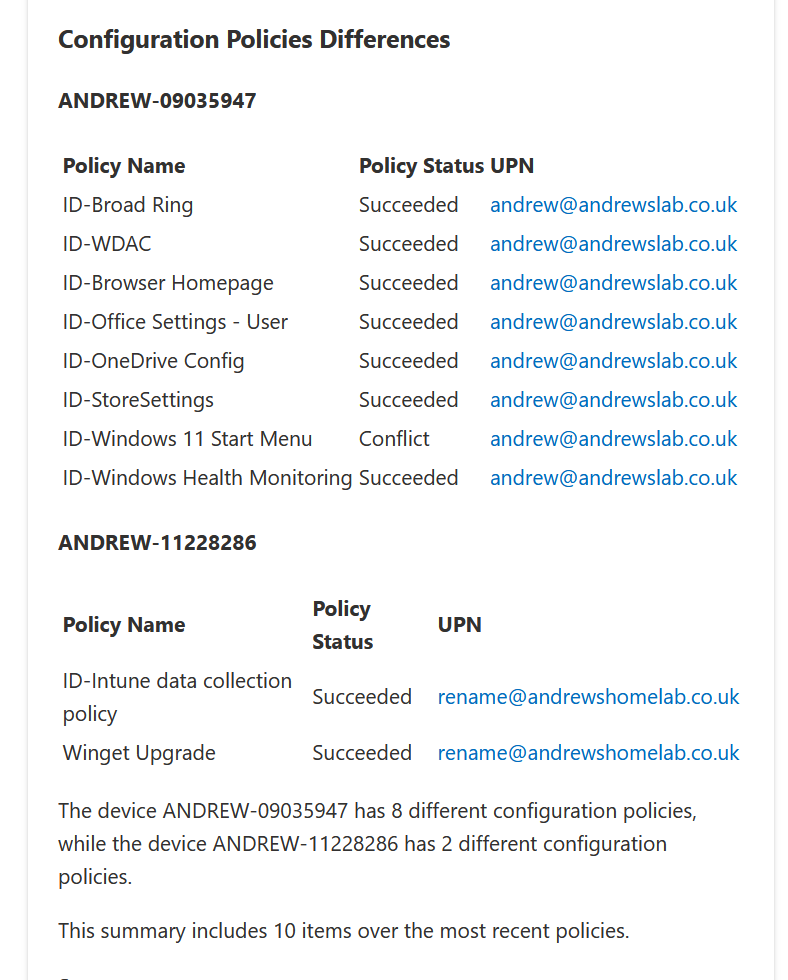
- Compare this device with another device – This STILL has an annoyance which has been there from the start, you have to manually enter the second device details. Surely a lookup would be possible these days! After selecting a second device, you can then decide what to compare against and for this, I want to look at configuration profiles, they usually cause me the most pain. This did give some half-decent comparisons, but it only listed 10 policies which if I am troubleshooting, isn’t really enough. I need everything! Usefulness: 4/10
- Show apps on this device – You can look for Managed Apps or Discovered Apps and optionally search for an app. It works absolutely fine, but these are easily available in 2 clicks anyway so you’re not saving much time. Usefulness: 2/10
- Show policies assigned to this device – Select from Config, App Config or Compliance. Works fine, shows success/fail and the account used. Again, Device – DeviceName – Device Configuration shows exactly the same information. Usefulness: 2/10
- Show group memberships – You can look for an individual group, or just list them all. It does expand on what you can see in Devices – Device Name – Group membership as it shows more details about the groups themselves which could be helpful. Usefulness: 4/10
- Show the primary user of this device – This shows exactly the same as Summarize This Device and on my test took over 20 seconds to display what is there on Devices – Name – Overview screen. Usefulness: 0/10
For those licensed for EPM, you can also summarize elevation requests to check if there are any risks associated with the app being requested
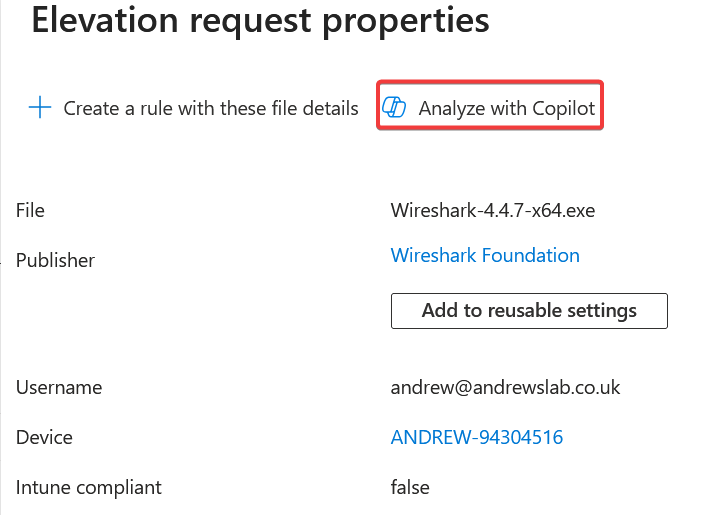
In this case, it’s all fine, but this will help when you’re in a rush, or have delegated these tasks and want some checks before approving
Not the best of starts so far, but we do have the all-new Explorer functionality to hopefully save the day…
Using Explorer
Explorer can be accessed via the main menu within Intune and gives a more traditional AI feel with natural language via a Search box at the top. There are also some suggested queries underneath
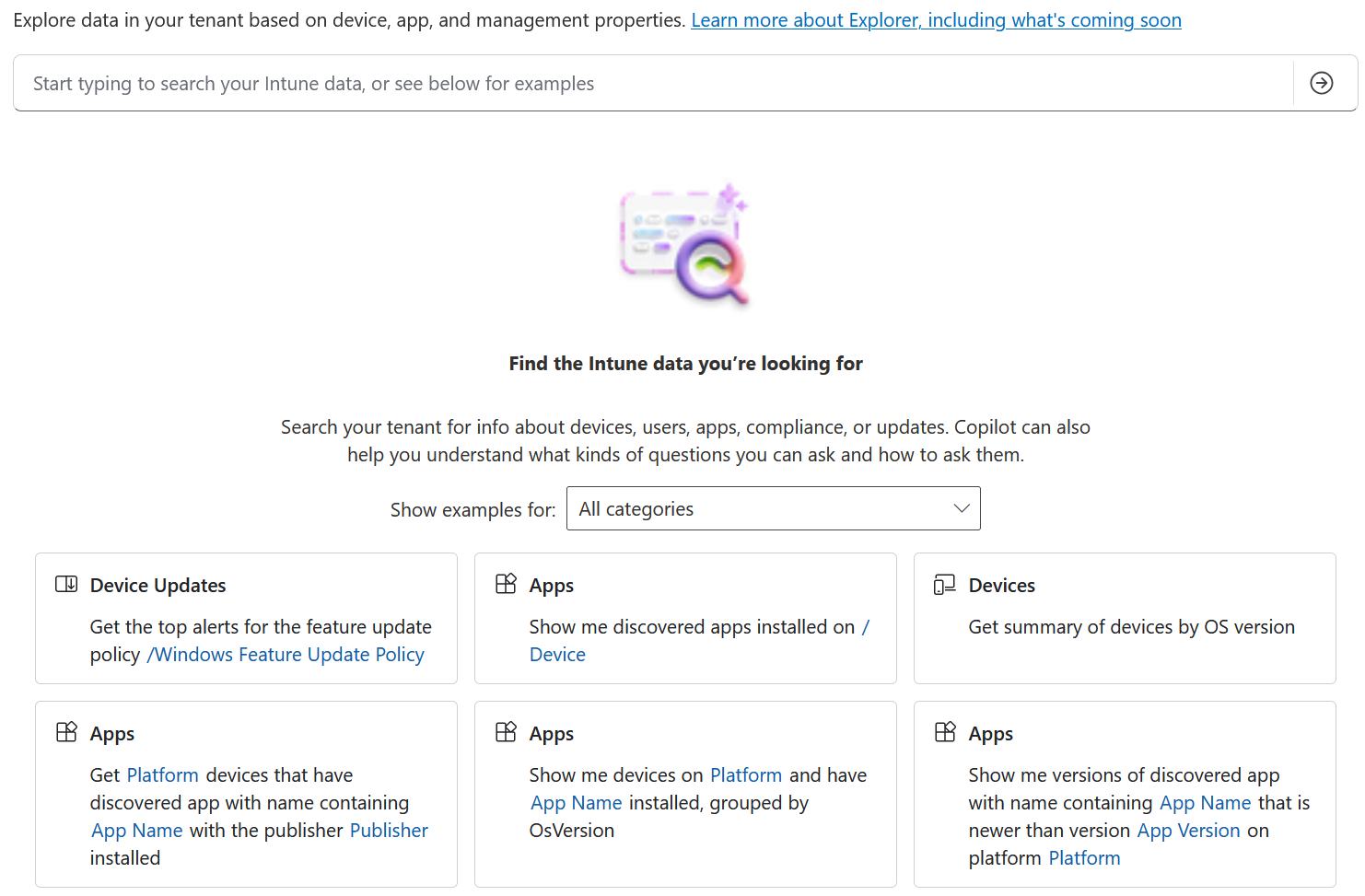
At present, it isn’t an entirely free text option, you can type anything you like, but still have a restricted number of queries you can actually ask it.
It is multi-device though so rather than having to click through each device, this will comb through the whole estate and there are some very useful queries in here, a couple of my favourites are listing devices which haven’t been updated and also a list of the different versions of apps across the estate.
It feels a lot snappier, the results come back quickly and from what I can tell are pretty accurate.
Each result gives “Next steps to consider”, but I found that a bit too generic and obvious, this was the output from listing non-compliant devices
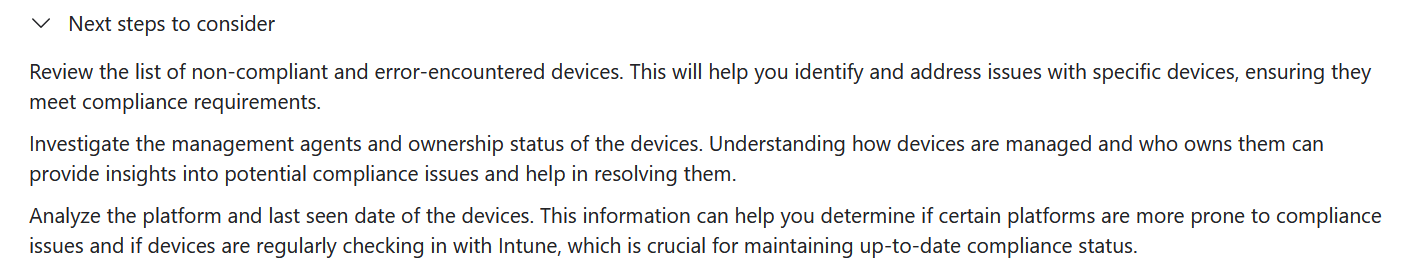
Query List
To make things easier for you to learn what is available before purchasing, this is what is there now (as of 14th July 2025):
App Configuration
- All received App configuration policy data
- Find users running managed mobile apps with an app configuration policy and an OS version of X
- Get the managed apps with an app configuration policy and an OS of X
- Get managed mobile apps with an app configuration policy and Intune SDK of exactly X
- Users with devices which haven’t checked in since X with an app configuration profile applied
- Get users with managed app called X who haven’t checked in since X
- Get managed mobile apps with an app configuration policy and Intune SDK greater than X
- Get managed mobile apps with an app configuration policy and Intune SDK which is NOT exactly X
App Protection
- Get users using a managed mobile app with the name Managed Mobile App Name and have an App Protection Policy applied and have devices where the last check in with Intune is before Last Check In Date Time
- Get managed mobile apps that have an App Protection Policy applied, and the Intune App SDK version is Mam Sdk Version
- Show me all received App Protection policy data
- Get managed mobile apps that have an App Protection Policy applied and are running on OS Version Os Version
- Get managed mobile apps that have an App Protection Policy applied and are running on OS Version less than Os Version
- Get managed mobile apps that have an App Protection Policy applied, and the Intune App SDK version is less than Mam Sdk Version
- Get managed mobile apps that have an App Protection Policy applied and are running on OS Version greater than Os Version
- Show me all users and apps that have received app protection policies
- Get users with an App Protection Policy with the name App Protection Policy Name and have devices where the last check in with Intune is before Last Check In Date Time
Apps
- Show me users that are not on OS version Os Version or newer of Platform and also don’t have Publisher App Name installed
- Show me users that are not on OS version Os Version or newer of Platform and have Publisher App Name installed, grouped by AppVersion
- Show me devices on platform Platform that are on OS version older than Os Version and don’t have App Name installed
- Show me users that are not on OS version Os Version or newer of Platform and also don’t have App Name installed
- Show me users on Platform and also don’t have version App Version or newer of Publisher App Name installed, grouped by OSVersion
- Show me what % of all devices have App Name version App Version or newer installed
- Show me users on Platform that have Publisher App Name installed, grouped by AppVersion
- Show me apps on Platform that have the most users on a version other than the latest
- Show me devices that have App Version or newer of Publisher App Name on Platform
Compliance
- Get Platform devices that are Compliance due to the compliance setting Compliance Setting Name
- Get devices that are noncompliant due to not having any compliance policy assigned
- Get Platform devices that are Ownership owned and are Compliance due to the compliance setting Compliance Setting Name
- Get Platform Devices that are Compliance
- Get devices that are Ownership owned and are Compliance due to the compliance setting Compliance Setting Name
- Get devices that are Compliance
- Get devices that have Compliance set to “NONCOMPLIANT” or “ERROR”
- Get Platform devices that are noncompliant due to not having any compliance policy assigned
Device Configuration
- Get device configuration policies that are not of the type Device Configuration Policy Type Name
- Show me Device Configuration Policies that contain setting Setting Name, filter by policy type equal to Device Configuration Policy Type Name
- Get device configuration policies that were not created from the template /Device Configuration Policy Template
- Get device configuration policies that have the status Device Configuration Policy status
- Get policies that have settings configured where the setting name contains Setting Name
- Get device configuration policies that are of the type Device Configuration Policy Type Name
- Get policies that have settings configured where the setting name contains Setting Name and the policy has the status Device Configuration Setting Status
- Get device configuration policies that were created from the template /Device Configuration Policy Template
Device Updates
- Get devices that are up-to-date for driver update policies targeting Driver Name, where devices that are ready to restart are included as up-to-date
- Get the statuses of devices that have a driver with the driver class Driver Class
- Get the statuses of devices that have a driver with the name Driver Name, the driver policy name /Windows Driver Update Policy, the driver publisher is Driver Publisher, the driver class is Driver Class, the driver publish date is Driver Publish Date, and the driver version is Driver Version
- Get devices with a feature update policy that still need to get the version Update Version of the feature update
- Get the top alerts across all Windows driver updates
- Get devices that are up-to-date for feature update policies targeting Feature Update Name, where devices that are ready to restart are included as up-to-date
- Get Windows devices that are on OS Version Os Version
- Get the current update states for each expedited quality update for device /Device
- Get the current status of devices for the latest expedited update
Devices
- Get Platform devices that belong to /User that were enrolled by /User
- Get devices of hardware model Hardware Model that have not checked in with Intune since before Date
- Get Platform devices that belong to /User where the jailbroken state is Jailbroken
- Get me devices that have cellular hotspot set to True False
- Get Platform devices enrolled by /User that have a compliance grace period ending before Date
- Get Platform devices that were enrolled before Date
- Get devices of hardware model Hardware Model
- Get devices that have serial number equal to Hardware Serial Number
- Get summary of devices by Cpu architecture
That’s our list of queries, whatever you type in the box has to somehow link to one of those.
AI obviously isn’t magic so it is just querying existing data, I know what you’re thinking because I was thinking the same, “couldn’t I just grab this myself with Graph?”. Obviously the answer is yes, but is that a good use of your time considering these are already built for you rather than having to find the endpoints, deal with pagination and also potentially with the hideous reporting endpoint.
Graph?
I can’t try some new features without working out what’s going on underneath and this is no different. Looking at the network traffic, it’s going to a whole new Graph endpoint at https://graph.microsoft.com/beta/deviceManagement/managedDeviceResourceQuery
It sends the query with a POST request with a KQL query attached. After submitting the request, it grabs the ID and then queries the status of it via a GET request to https://graph.microsoft.com/beta/deviceManagement/managedDeviceResourceQuery/retrieveQueryStatus(queryRequestId=’ID-GOES-HERE’).
When the queryRequestStatus changed from inProgress to Completed, it sends a final POST request to https://graph.microsoft.com/beta/deviceManagement/managedDeviceResourceQuery/retrieveQueryResult with the Request ID within the JSON and the result is returned in JSON format.
Testing in Graph explorer, the endpoint is a 403 forbidden so it’s UI only for now unfortunately.
Final Thoughts
The big question everyone is asking, is it worth it? Prior to adding Explorer, my answer was usually no (and I have burned through a LOT of Azure credits finding this out). Adding Explorer, however, has really changed the game.
Whilst the queries aren’t going to change your life, these are exactly the sort of questions coming from your C-Level execs, or the type of day-to-day monitoring you should be carrying out. Instead of spending a few days getting the report data together for the next board meeting, you can click a few buttons and have live data available in an instant.
This is also a great selling point when making your business case. How quickly do they want the report data, if they want it quickly and regularly, pay for the SCUs. It is also useful having everything in one location, although a multi-request would be useful, “show me this AND this”
Similarly, you can give your Service Desk staff access to Copilot to quickly check for any issues ahead of them being discovered by users (or bad actors depending on the severity).
So, would I pay for it in it’s current state. The answer to that is “probably”. For larger estates, getting the report data you need quickly is priceless, especially with execs breathing down your neck because the meeting is in an hour and they forgot to tell you when they booked it 6 months ago.
For smaller shops, chances are you are spinning many plates and whilst the report data might not seem critical to you at present, there are things which should be monitored by everyone for a secure environment. Chances are you don’t have time currently to be pro-active and are busy putting out fires all day every day. Security Copilot can help with that and free up your time for more useful tasks.
There are some things that could do with improving a bit (can we have Clippy back please Microsoft?), but this is new technology and I am looking forward to seeing how it progresses!

Thank you fir this great Article Here, helps me a lof with intune.