Update: Update Compliance is now EOL, please use Windows Update for Business reports instead:
Today’s post is about a Microsoft tool which is completely free and a great way of tracking Windows updates across the estate. Did I mention it’s free?
If you want to read up more about it, here is the Microsoft official page. For this post, I will cover the deployment and configuration of it.
Before I start, it’s worth noting that if you already have Desktop Analytics deployed, you need to use the same Resource Group and Log Analytics Workspace.
First up, keep things neat and create a resource group in Azure
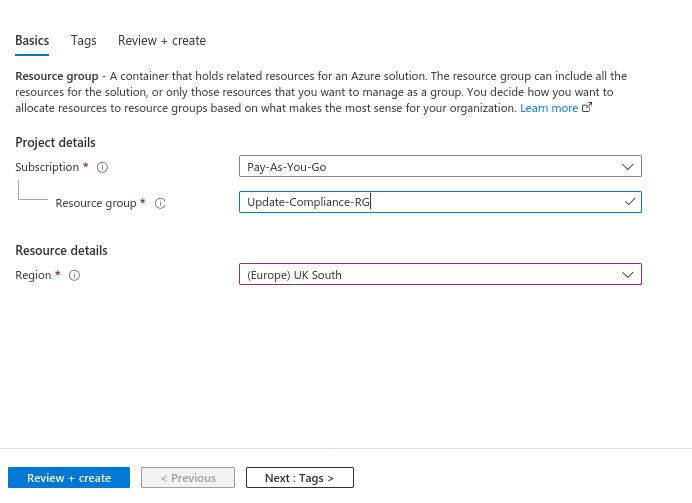
Now, create a Log Analytics Workspace inside the resource group. Don’t worry about any mention of data charges, they are free for this purpose
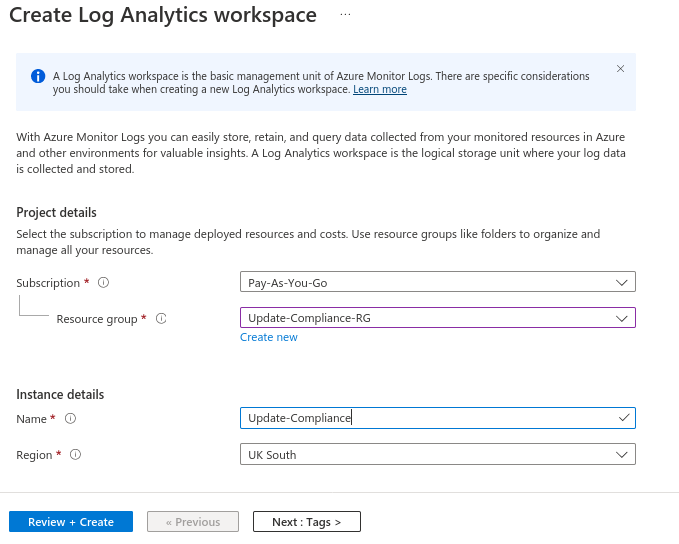
Once that is built, go to the Marketplace and find Update Compliance
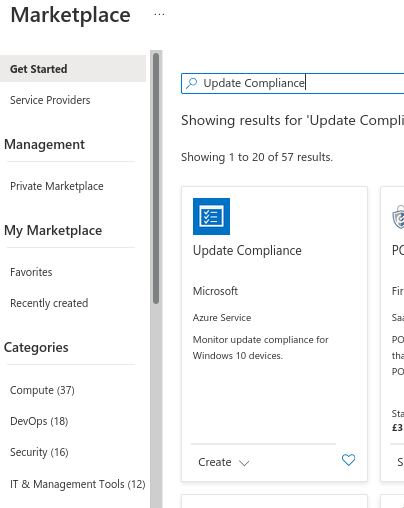
There aren’t any configuration items at this point so go ahead and create it
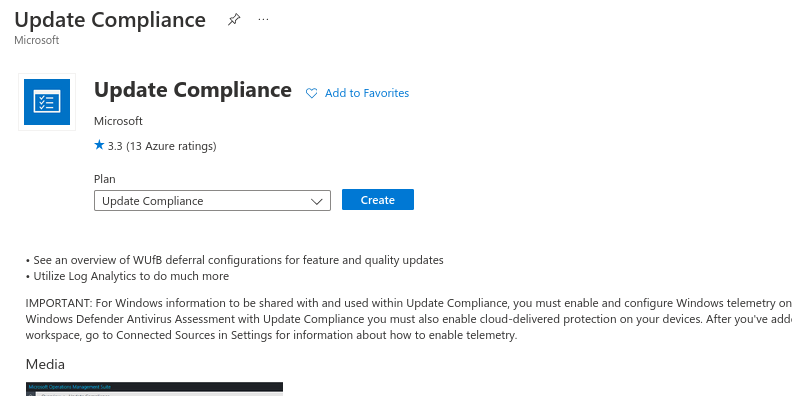
Point it at your new Log Analytics Workspace (or Desktop Analytics if you use that already)
When completed, click Go to resource group
In the new resource, click on the Solution (WaaSUpdateInsights)
Now click on Update Compliance and copy the Commercial Id Key
Now we need to configure a Profile in Endpoint Manager to point the devices to the Log Analytics Workspace via a Custom OMA-URI policy
For the rows, the details can all be found here (I’ll include below as well to save having to cross-navigate)
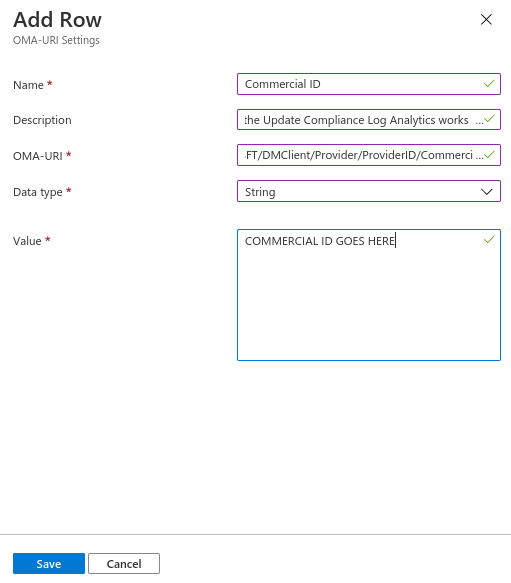
Set the Commercial ID:
OMA-URI
./Vendor/MSFT/DMClient/Provider/ProviderID/CommercialIDSet the diagnostic level (minimum of 1, but feel free to increase)
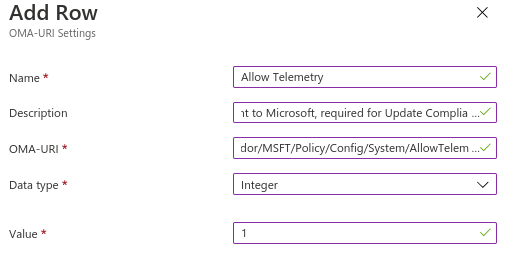
./Vendor/MSFT/Policy/Config/System/AllowTelemetryDisable opt-in to stop users changing the setting
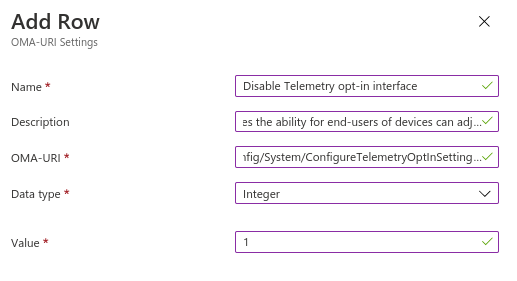
./Vendor/MSFT/Policy/Config/System/ConfigureTelemetryOptInSettingsUxWe need to Allow device names or nothing will show
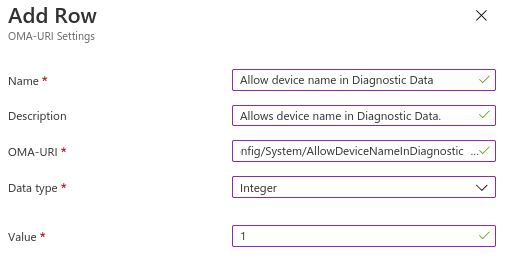
./Vendor/MSFT/Policy/Config/System/AllowDeviceNameInDiagnosticDataAnd the final row is newly added, but essential to allow Update Compliance Processing
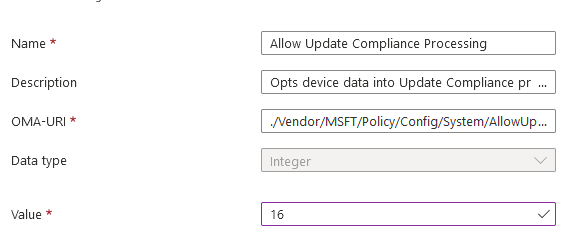
./Vendor/MSFT/Policy/Config/System/AllowUpdateComplianceProcessingOnce the data starts coming through, navigate to the Log Analytics Workspace and click on Workplace Summary
Once the data has processed, you will see data about the devices, which have issues and what the issues may be

Plus pretty graphs to share with management:

I always try and deploy this for anyone using Intune, it isn’t complicated to deploy, costs nothing and can save a lot of time reporting on updates

Hi Andrew,
Is there a requirement for this to work i.e., M365 E3/5 and AAD P1 or even P2? Got some client machines that only have Intune Device Licence and wondering if this would suffice?
We also have around 500 devices would this mean this stays free and there be no extra costs?
Great guide btw!
Ta
Hi, the requirements are basically on the device side so you should be fine with your device licensing (requirements are listed here).
Definitely no extra costs as long as you don’t add anything else into your log analytics workspace.
Hi Andrew,
Great guide. I ran into an issue and noticed an error.
I think the AllowUpdateComplianceProcessing integer value should be set to 16 rather than 1 as per the Microsoft guide.
Hi Ryan,
Well spotted, thank you! Have updated now
Hello Andrew,
Is creation of log analytics workspace is also free or chargeable?
That’s also free, a log analytics workspace usually charges on data ingest, but it’s free for Update Compliance and Desktop Analytics