With the release of MAM for Windows I thought I would revisit securing your data on BYOD with Windows (previous post here)
In this post we will cover how to fully protect your data so that your Windows users can only access corporate information via a protected browser and keep the data contained.
To make things easier, I’ve also included everything in a PowerShell script here (note: CA policies are disabled for you to manually enable and add exclusions as required)
Updated 15/02/204 with fixes
Device restrictions
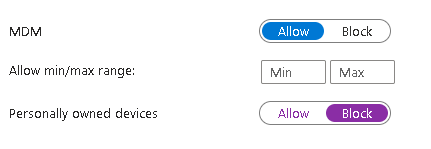
The first thing we need to do is block BYOD enrollment via a Device platform restriction policy:
Enable MAM
Now we need to enable MAM by opting into the preview here:
https://aka.ms/mamforwindowspublic
After opting in you will get a new link to access the Intune console and enable the Windows MAM option
In Tenant Administration, click on Connectors and Tokens and then Mobile Threat Defense.
Add a connector for Windows Security Center:
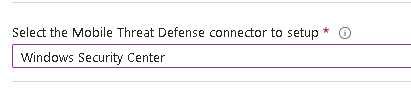
Don’t worry if it displays as unavailable, it will update when used.
Configure MAM
Next, click on Apps and App Protection Policies
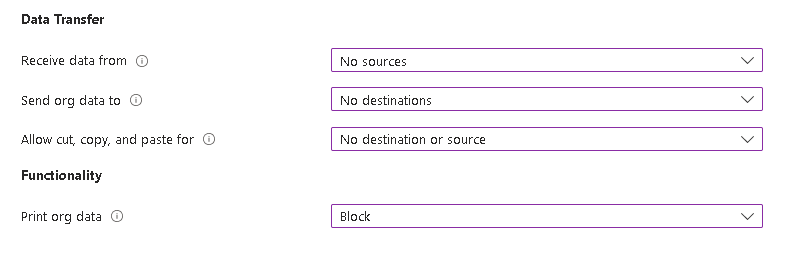
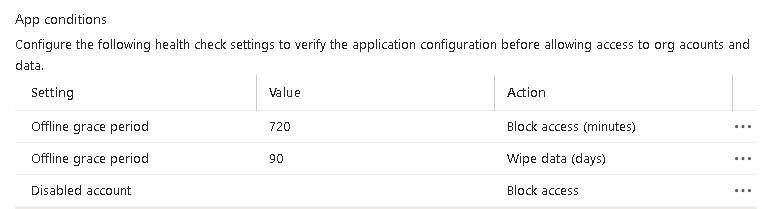
Create a new Windows policy (not Windows Information Protection). Select Microsoft Edge and configure as required:
Now we have completed the Intune side, we need to add extra security in Conditional Access
Block anything but web access
First we need to block non-corporate devices from accessing anything but the web app by requiring compliance. As MAM uses APIs to configure the browser, a simple block won’t work here so instead we will grant, but require compliance which is effectively blocking BYOD
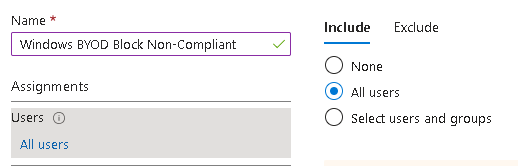
We only want O365 here, otherwise we block the API
Add some conditions:
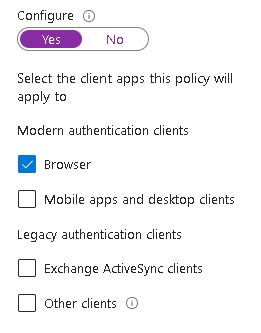
We want to let the browser through on this one, we will protect that on the next policy:
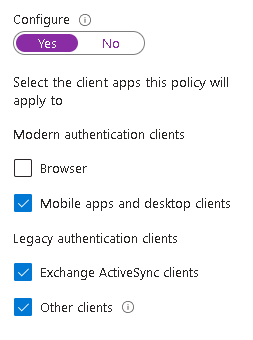
As mentioned, we will exclude corporate devices:
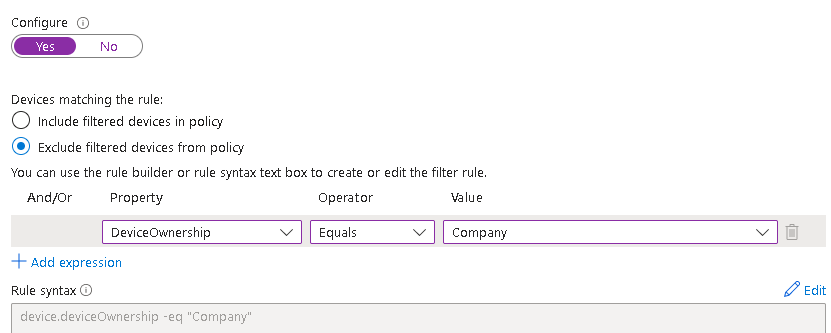
Then require compliance which will automatically block non-corporate devices:
Restrict Web Access
Finally we want to lock down the browser access with a second CA policy
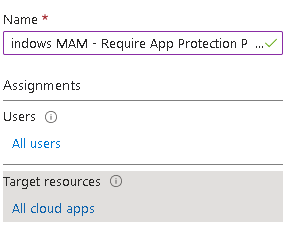
Add some conditions:
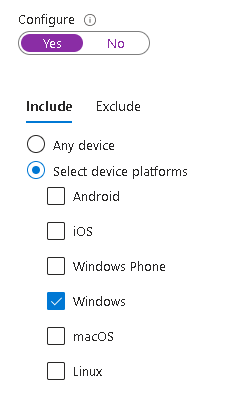
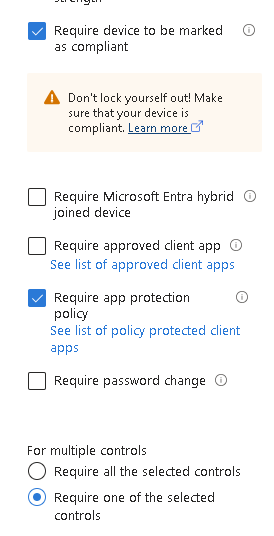
This one is important or the policy will fail to create:
Most important of all, we need to require app protection in Grant controls. We will also add compliance here to let through any corporate devices:
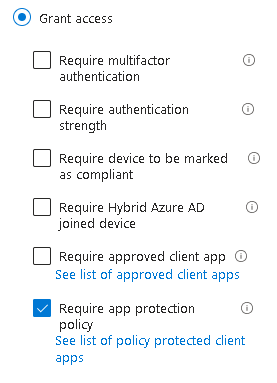
As an extra layer of security, you can also Block downloads using Conditional Access App Control in the Session controls:
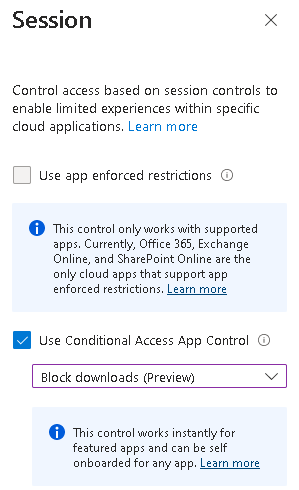
One thing to note when logging in from here:
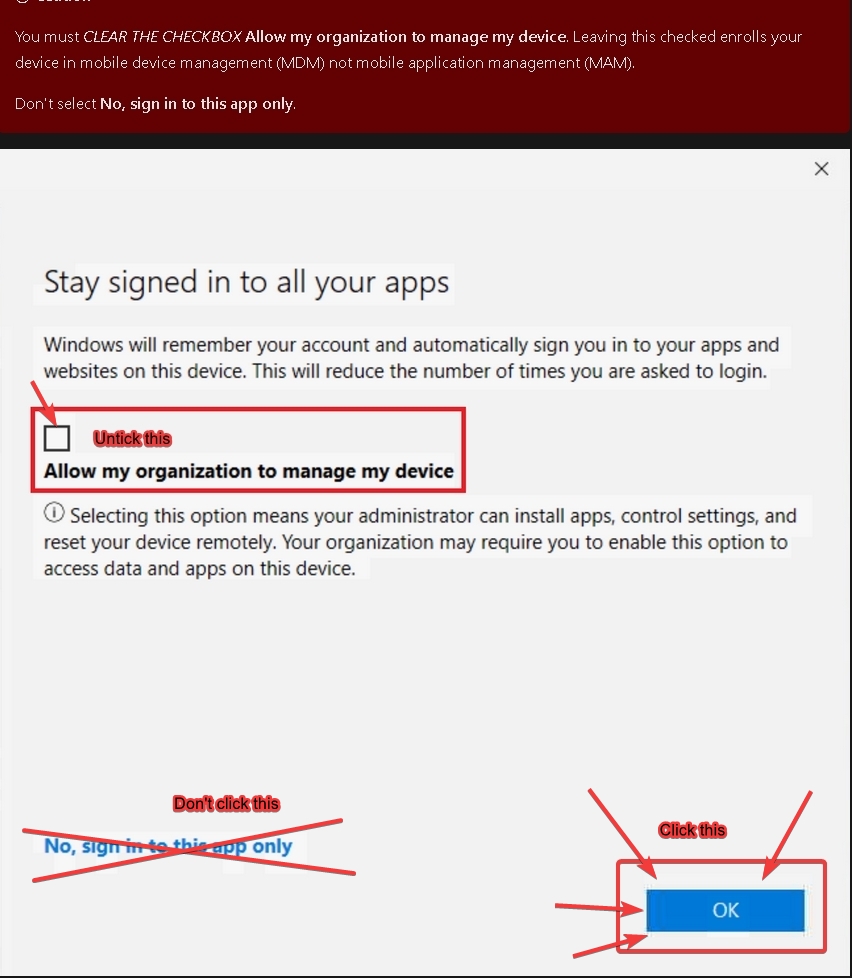
Hope this is of use!

Hello! I’m testing MAM for a few users, my problem is that after logging in into the m365 service (I have allowed office 365 app and Sharepoint online for MAM) the webpage says I need to login into Edge with my work account. When I do so, I receive a message that “you can’t get there”, which is triggered by another CA blocking access for non-compliant and non hybrid-joined devices. That probably means Edge profile login is using some cloud application which is restricted by that other CA, but there’s no way to exclude Edge (I’ve only found an Edge management service as cloud app, but it didn’t solve the problem). Somebody said to exclude MAM from the non-compliant-non-hybrid CA rule, that would make sense but how do you accomplish that?
Hi,
If you change your existing CA to require Compliant, Hybrid or App Protection, that should let the browsers register
Hi, Thanks! That did it 🙂
I was able to get this setup but have a question on the assignment of the MAM policy for Edge in Intune. How do you recommend doing the assignment? I suppose I could assign it to all users but then the MAM policy is still applicable to corporate owned devices. While it wouldn’t be enforced by CAP, is there any reason to try and makes sure the MAM policy assignment doesn’t hit corporate owned computer? It doesn’t seem like there is a lot of uplift on security to have the MAM policy being assigned to corporate owned devices if you’re controlling access in general on those devices via a CAP that requires compliant device.
I would assign to All Users and then use Filter for devices to only include non-corporate ones
Is there a way to prevent the work profile from being synced to the browser? For instance, if I enable MAM for Windows and a user accesses a computer at the library, they might simply exit without signing out. This could allow subsequent users to access their profile. How can we mitigate this risk?
There isn’t a way with MAM, it uses the work profile to authenticate. You could turn down the session times when offsite, but there will still be a risk. This one is just user training sadly
What would need to be done in order to have this same approach work on a MacOS device?
At the moment there isn’t anything similar for macos, I normally suggest AVD or Windows 365, but obviously there is a cost involved
Thanks Andrew, really useful guide. I’ve found the feature to be a step in the right direction. Is there anything that you were able to do around restricting sites within the managed MAM profile? I know this feature is available for iOS and Android, but I couldn’t find anything for Windows app protection. In my testing, it still allowed me to copy data within the work container/profile to untrusted sites e.g., personal mail etc.
I don’t think that’s yet available for Windows, it would require MDE or other web filtering, but these are apps in themselves so wouldn’t work on a BYOD
No luck, I’m afraid.
I have noticed that if I change the CA policy’s grant to be either compliant or require APP (so it could also allow managed devices through), the failures are that the device isn’t compliant.. It seems the app protection policy isn’t applying, despite confirming its deployed and targeting the user.
If set in grant to only require APP, the failure is that required APP is not satisfied.
Does your edge browser profile login OK? I found once that happened, the APP applied correctly. I also hit sign in to this app only the first time which didn’t help
Yes. And I can even tell that the APP is actually working since when I’m in that work profile in Edge, I tried to download a file (since I have it restricted in policy), and I get pop-up that the organization has blocked downloads.
Do you have downloads blocked in the CA policy as well? It could be that and not APP happening
Just confirmed my CA policy – nothing configured in Session.
Further testing – confirmed policy works on another device that is running Windows 10. Without Changing anything, retried on the Windows 11 client I had been using, and still fails. Really odd.
I will have to do some more testing, I think my test machine may have been running Win10 as well
Were you able to reproduce this issue on windows 11?
Just tested on a brand new Win11 VM and it all worked fine, MAM policy applied and CA worked ok
Just tested on another Windows 11 device and also works. Thats great but also concerning why it didn’t work on other device.
Did you have success with Mobile Threat Defense with Windows Security Center? Mine still shows as not setup and seems to follow that pattern, since I set policy’s max threat level to “secured” yet access works even if I disable Defender’s real time protection.
Mine is also showing Not set up as well. I’ll see if I can find out why!
Any luck with Mobile Threat Defense? Microsoft has been giving me the runaround going from Intune Support to Azure, back to Intune and now saying its Windows issue.
I am making progress, should have an update soon
Awesome article, thank you!
Been trying to get this setup in our tenant but keep running into issues with the CA policies. I was seeing it throwing a fit about my test BYOD device when using the device matching rule – whether to include personal or try excluding company.
So I took that out entirely to test further and now it fails saying there isn’t an app protection policy – when I’ve confirmed its setup and targeting user..
Seems rather odd and noticing others having similar issues – https://www.reddit.com/r/Intune/comments/1aqpi8w/ca_issues_setting_up_mam_for_edge/
Hi,
I am having similar issues as well and I also can’t see why it’s happening. Am doing some further testing and as soon as I have a fix I will update the post
Just updated it now, can you see if that works please
I have the Same issue, we have set up a CA for all devices need to be compliant (onboarded in intune), we excluded the browser
then i set up your CA like above .. what if shows it correctly
however, once i log into edge on boyd with the account, it fires always “you cant get there from here” after
could it be that, edge sync login does use Desktopclients as “client-apps” and not browser ?
Can you check the sign-in logs to see what the device details are? That should tell you which app is being used
yes indeed :
Client-App
Mobile Apps and Desktop clients
Appliaction
Microsoft Edge
so, how would i do, think exclude of edge is not possible in CA ?
Mobile Apps and Desktop clients cant exclude this one also because i dont want data on personal devices
any ideas ?
I’ll build a VM and do some testing, will get back to you ASAP
Not working for me I think, I add user in the group, and when I am trying to log in Edge, it is saying this : https://i.imgur.com/zHHSoZg.png
When I do it, I have this : https://i.imgur.com/ao2YQAX.png
Is it because we block Personally own device in the first step ?
You need personally owned to be blocked for this to work.
It might be using the Conditional Access What-If tool and look through the sign-in logs to see what’s happening
Maybe the problem https://i.imgur.com/T3pMVj4.png ?
Here the sigin log opf the user : https://i.imgur.com/6lj6ouR.png
Do you have other CA policies configured? Blocking non-compliant devices is good, but you should have an exception for MAM
No, I only have these : https://i.imgur.com/e6XrzxD.png
CA starting by BYOD MAM are the two created with your script.
I see in the comments here that Duck has the same problem as me.
Can you check that browser is excluded from the compliant devices policy.
Also, on the sign-in logs, have a look at the device info to double check it’s coming from Edge
Wow cool script!
What the purpose of the group Windows BYOD Users ?
It’s to give you more control over who can use BYOD on Windows. If they aren’t in that group, the policy won’t apply so they will be blocked by CA
Cool I am trying it, my user is in the “Windows BYOD Users” group.
When I try to connect from Windows device, from Edge, it blocking me saying :
Log in with your professional account
To access your service, application or website, you may need to sign in to the Microsoft Edge browser profile using [email protected] or enroll your device with lab.flo 🦖 if you are already signed in.
Is it normal ?
Is your Edge browser logged in with a work profile?
No because it is a personnal device.
Do I have to log in for everything to work?
Just into the Edge profile itself
Hi Andrew, just to understand.
If a device is BYOD, so non compliant and using WINDOWS APPS, it will be blocked.
If a device is BYOD, so non compliant and using BROWSER, it will be granted, and protected by the App Protection Edge Policy right
Is it right ?
What about chrome/firefox ?
Thanks
That’s correct.
Chrome and Firefox would be blocked as app protection is currently only Edge
Running into issues with the compliance part of this. All devices I try and join say they do not need organisations compliance requirements, see device management portal for why it’s non compliant. Maybe I’m looking in the wrong location, but I can’t find anything that is saying why it’s noncompiant?
Thanks for the guide!
Does the WhatIf tool in CA say anything? Might be worth checking the Entra logins too
Hi all!
Program Manager from Microsoft working on this project here 🙂
We are very excited about this feature and would love your feedback. Yes, there is a sign up needed for Public Preview. Please see this document for more information: https://aka.ms/mamforwindowspublic.
Please be mindful to not share information from the Public Preview Teams channel outside of that channel, as we are still working to make this the best possible feature we can.
Thanks,
Jordan
Thank you Jordan 🙂
I had the same results and eventually found this sign up form for the public preview
https://forms.office.com/Pages/ResponsePage.aspx?id=v4j5cvGGr0GRqy180BHbR5Et9AHvwQBCvdYzt0-Gxb9UM1NFWVRUTlhMUEIwWEc2VTZKUjYwUVk2QS4u
This is really good, thank you.
When I try to do this manually and select app, I have no apps available to select from so I cannot select Edge.
I think as it’s still in preview the functionality is still rolling out. Might be worth an MS ticket within the portal