I often find myself having to create the same selection of Entra ID groups when deploying a new Intune environment and whilst the Entra Portal is easy to use, I always look to find a way to cut down how long each task takes. The more I can automate, the more I can get done in a day.
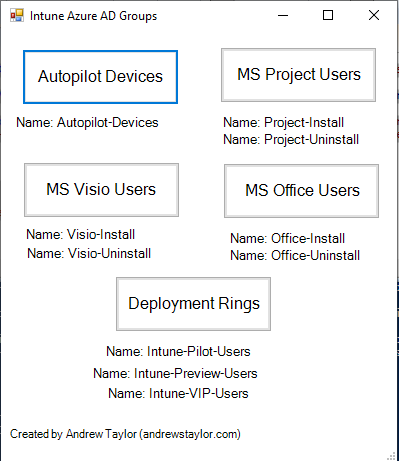
To that end, I have created a new PowerShell script to automate the creation of the following groups:
As always, my script is available on GitHub here or on the PS Gallery
Install-Script -Name create-intune-groups- Autopilot Devices (a dynamic group on the ZTID)
- Microsoft Project Install (a dynamic group based on users who have a MS Project license for desktop apps applied to their account)
- Microsoft Project Uninstall (those who don’t)
- Microsoft Visio Install (a dynamic group for users who have a Visio license for desktop apps)
- Microsoft Visio Uninstall (those who don’t)
- Microsoft Office Install (a dynamic group for users who have O365 Enterprise Apps license)
- Microsoft Office Uninstall (those who don’t)
- Deployment Rings Groups – Preview Users, Pilot Users and VIP Users (Static, assigned groups)
The script can be called programmatically using a parameter (GroupName) with the options of Autopilot, Visio, Office, Project or Deployment. For example:
create-intune-apps.ps1 -GroupName AutopilotAlternatively, if no parameter is supplied, it will popup a small GUI with buttons to create the groups:
The script uses the Microsoft Graph module which it will install if required and load upon launch.
After that, the PowerShell command New-MGGroup sorts out the group creation. As an example, for Project Users:
New-MGGroup -DisplayName "Project-Install" -Description "Dynamic group for Licensed Project Users" -MailEnabled:$False -MailNickName "projectinstall" -SecurityEnabled -GroupTypes "DynamicMembership" -MembershipRule "(user.assignedPlans -any (assignedPlan.servicePlanId -eq ""fafd7243-e5c1-4a3a-9e40-495efcb1d3c3"" -and assignedPlan.capabilityStatus -eq ""Enabled""))" -MembershipRuleProcessingState "On"As you can see, we are creating a Security Group (non mail-enabled) with the dynamic membership rule applied which queries the users servicePlanId.
If you are creating these manually, make sure the capabilityStatus is set to Enabled. Once a user has a license assigned, that serviceplan remains in place throughout and the status switches to Disabled. If you miss off that part of the query, removing a license will not remove them from the group (I found this out the hard way!)
Hope you find this useful.
