Welcome, in this post I’m going to look at the Monitor tools in Devices within Intune, an icon I’m sure you’ve all seen, but rarely clicked on:
What lies inside these icons I hear you ask, well, it is a wealth of information covering the vast majority of settings within Intune, although it’s a bit light on Updates (but fortunately we have Update Compliance to tick that box)
Assignment Status & Assignment Failures
The first two options are for the status of policies and any assignment failures with figures on the total status of each policy. If you click on a policy, it will take you directly to it to drill down further

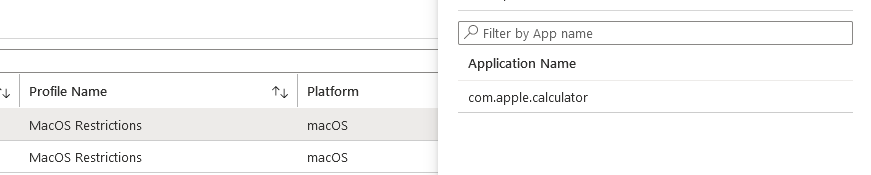
Devices with Restricted Apps
If you have any policies with restricted applications (in my case for MacOS), this will list any machines with the apps present and clicking on the row will display which application has been detected
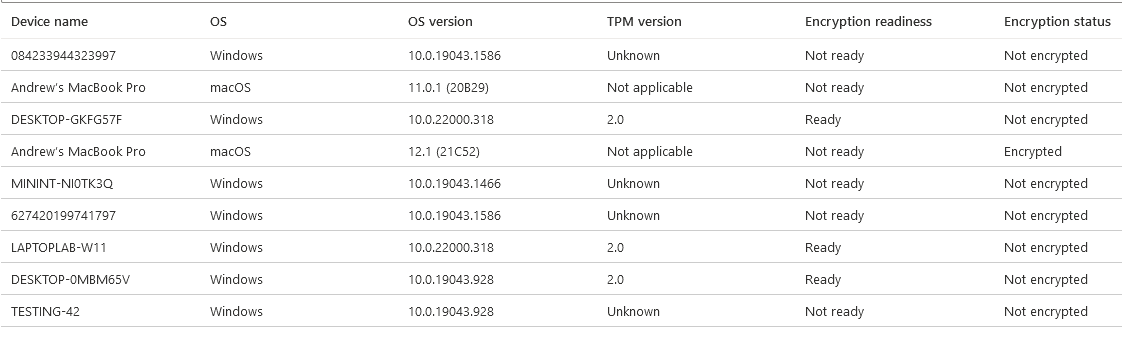
Encryption Report
This one is pretty self-explanatory, but does show some good information on the TPM version and which machines are encrypted. The Health Attestation Report (below) goes into much greater detail though
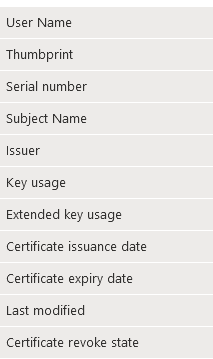
Certificates
This is a particularly useful one if you have certificates deployed to your devices as it shows full details of the certificate, including the expiry date
Compliance – Non Compliant Devices
Now onto Compliance policies, this one gives a quick view of any non-compliant devices, useful if you aren’t as strict as me and don’t block access (hence mine remaining empty)
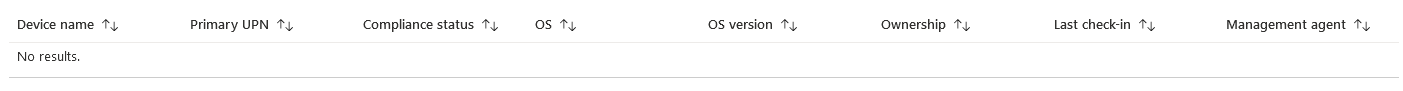
Devices Without a Compliance Policy
Always a good one to keep an eye on, no point having compliance policies and conditional access policies in place if you have machines which have slipped through the net!
Whilst we’re on the subject, to be on the safe side, make sure this is Not Compliant
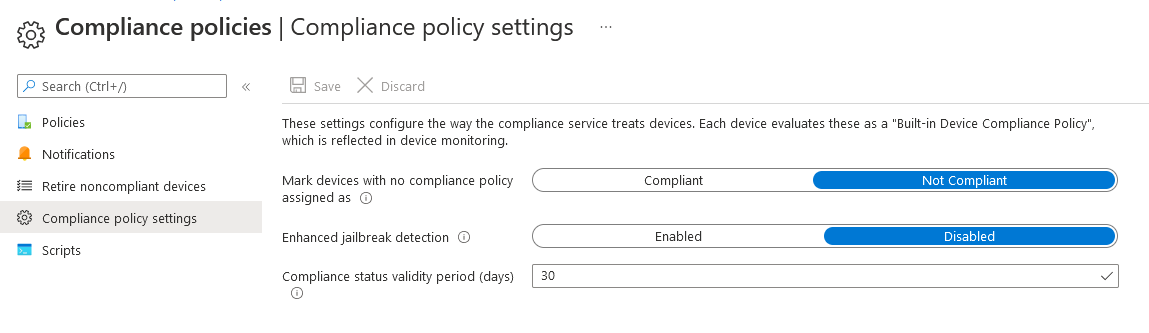
Setting Compliance
This shows the device compliance against the built-in compliance policy which is fairly relaxed. If you have devices not in compliance in here, they need looking at
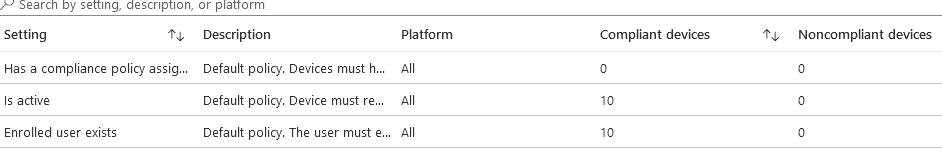
Policy Compliance
This shows the compliance against any custom policies you have created

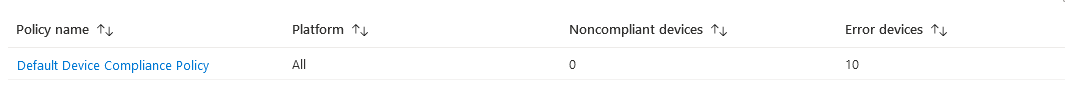
Noncompliant Policies
Rather than at the device level, this looks at the policy level and shows which policies have non-compliant devices assigned. If you have multiple compliance policies, devices may just be showing as non-compliant. This gives a view of where the issue lies and might point out an overly strict policy
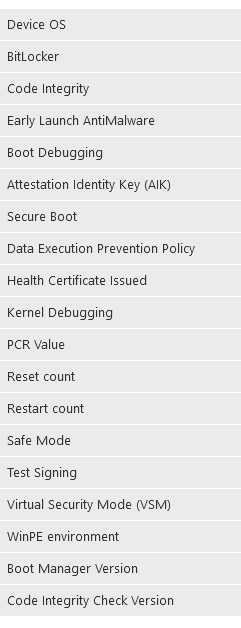
Windows Health Attestation Report
This is one of the most thorough reports (and most useful in my opinion). If you are troubleshooting any bitlocker issues, it’s the first place to look. This page shows everything you need to know about the device from a security/BIOS/encryption aspect. It also has filtering in place for larger environments
Autopilot Deployments
In this section we can see all Autopilot deployments over the last 30 days including the device details, user details, which profile was used and even how long it took. If you use Autopilot, this is worth looking at even if it’s just for a timescale on how long a deployment takes
You can also sort by total time to check for any which seem to be taking too long (and then you can dig into Endpoint Analytics to have a look at that machine and see why/replace the HDD with an SSD)

Enrollment Failures
Again, fairly self-explanatory, this shows failures for all users, or you can look for a specific user which is useful if they have received the Time-Out error within Autopilot and called you for help.
You can also click on the link for a graphical representation if you need to send a report to management
Incomplete User Enrollments
These are Company Portal led enrollments (not Autopilot) which didn’t complete due to:

Also in a nice graphical view
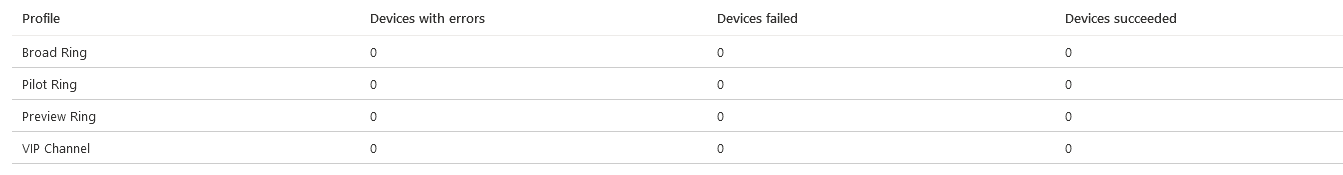
Per Update Ring Deployment State
Now onto Software Deployments, this first one shows how many devices in each of your update rings have picked up the deployment settings. You can click on the deployment ring to drill down and then I would normally grab device details and look further inside Update Compliance
Installation Failure for iOS Devices
This shows any failed iOS Update installs and often the reason why it failed so when a user complains they haven’t received the latest update, you can tell them to delete some photos to clear space with data to back you up.

Feature Update Failures
If you are using the new Feature Updates functionality to push out Windows 11, or Windows 10 21H2 etc. you can have a look here if any devices have failed to update and then drill-down as necessary. If it’s a Windows 11 failure, it’s worth looking at the “Work from Anywhere” report in Endpoint Analytics in case the device is not compatible
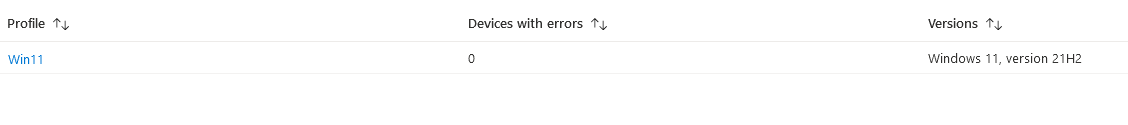
Windows Expedited Update Failures
Similar to the above, if you have an expedited update policy, you can have a look for device failures in here
Device Actions
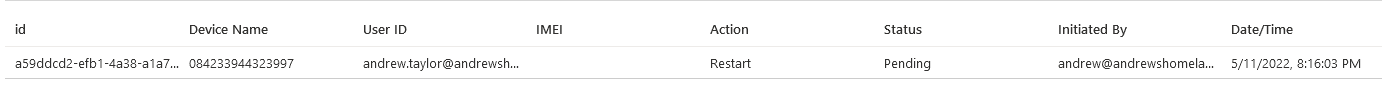
Finally, we have Device Actions where you can see who has sent which commands to which devices. If a user has called to ask why their machine has mysteriously rebooted, this will show you if it came from Intune and even who clicked it!
For anyone supporting an Intune environment, I’d always suggest having a browse of these fairly regularly so you can quickly spot any issues across the estate and it’s a lot quicker than checking policies individually!
I hope this has been of use, for Part 2, I’ll be looking at the Monitor section for Applications

Great article. How would I monitor and report unmanaged devices with an OS older than Windows 10 that say, have corporate Outlook installed locally and getting email?
If your email is on O365, check what your MAM registration settings are configured for?
You could also configure a Conditional Access policy to require devices to be managed (or compliant) and set it to Report Only which will flag up any non-managed devices using O365 apps
Thanks, is there a way to do it using compliance policies in intune? Also, your contact page has no contact info but maybe that’s by design 🙂